Passive tap (tap) of fast ethernet - IP "listening in"
Sometimes during deployment, it is necessary to capture network traffic between devices to resolve a problem to remove obstacles. In the case where one of the devices is a computer running software, it is often enough to have Wireshark software installed and check where the problem is. If we want to check the traffic between devices, it is necessary to intercept the transmission from the port of one of the devices.
In professional solutions, we can use the "port mirroring" function on the switch and we can "copy" traffic from the selected port / ports / vlan to another selected port where we connect the computer, eg with Wireshark software. In this way, we can intercept traffic at the interface speed, i.e. 1Gb / s or more (e.g. 10Gb / s), but at higher speeds there are significant requirements for devices that intercept and analyze the tested network traffic.
How can we deal in the "field" when we urgently need to examine the traffic between two devices in the LAN and we do not have a managed switch with the "mirror port" function, and we cannot install traffic analysis software on the devices (e.g. it is a router / printer pair / disk array / switch etc.).
Once a popular way was to use the outdated 10Mb / s hub, nowadays these types of devices are less available and limited bandwidth can be a problem.
We can use the 100Mb / s (fast Ethernet) passive tap method, which will allow intercepting network traffic between devices. It is a solution beyond all standards, which can even damage the equipment (in extreme cases). You can also "separate" yourself from the tap for greater security, e.g. with a fast Ethernet switch for ~ 40 PLN.
Use of the solution is at your own risk, but sometimes such a simple "tap" can be useful when troubleshooting network communication problems.
To prepare the "branch" I used two double 8P8C (RJ45) sockets,
to begin with, we connect the pins of one socket with the socket in the other module:
1 - 1 (TX +)
2 - 2 (TX-)
3 - 3 (RX +)
6 - 6 (RX-)
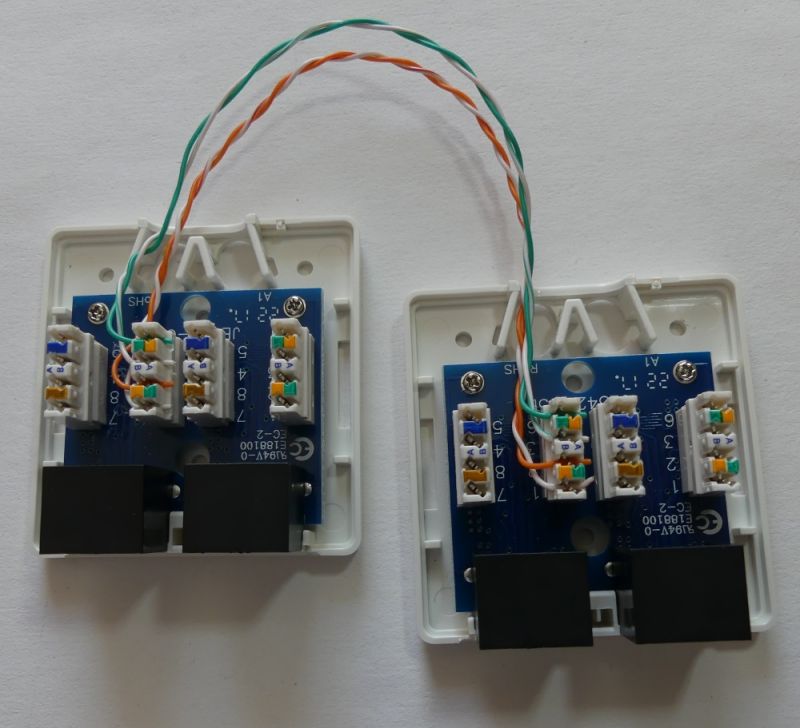
We get an "extension" that can work in the FastEthernet standard.
Then, in both modules, branch the transmission lines to the second socket. In one socket the transmitting pair (1,2), in the other socket a receiving pair (3,6). The pairs are branched to terminals 3,6 (RX +, RX-).
1 (TX +) - 3 (RX +)
2 (TX-) - 6 (RX-)
3 (RX +) - 3 (RX +)
6 (RX-) - 6 (RX-)
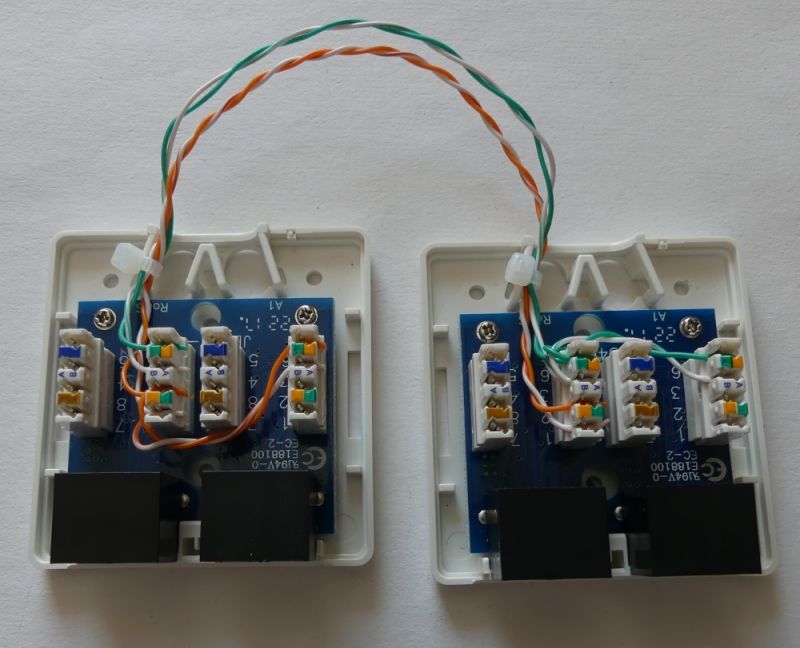
After closing the sockets, it is worth marking them so that the internal wiring diagram is clear to everyone:

Connect the device to the "Device" socket with a straight cable (patch), e.g. in the EIA / TIA T586B standard,
connect the existing cable connected to the interface of the device to the "Uplink" socket.
On Tap sockets we can intercept one-way transmissions "from the device" or "to the device". Connect a straight cable to the "Tap" socket and connect it to the network card in the computer with the Wireshark program installed. ifwe want to intercept the transmission in both directions at the same time, we need two network interfaces on the computer analyzing the traffic.
Due to the common AUTO MDI-MDIX (connection detection with a straight / patch or crossover / crossover cable), the transmission direction available on the Tap terminals is determined experimentally.
In my case, the traffic "from device to Uplink" was available on the "Tap" socket next to the "Uplink" socket, while the "Uplnik to device" traffic was available on the "Tap" socket next to the "Device" socket.
Passive Tap can be used only at your own risk (risk of damage / interference), in home conditions the "tap" may be useful to check the traffic between our home router and the operator's device with an Ethernet interface. You can check what communication is established by the home router and what traffic is coming to the WAN interface from the Internet. Attackers may try to use flaws in the software of cheap routers to build botnets or try, for example, to redirect us to a fake bank website, etc. Checking the router's communication with the Internet can detect anomalies. The device can be useful for education and experimenting with the LAN and for detecting problems with the devices launched (e.g. enc28j60).
What do you think about such a primitive way to analyze network traffic?
In professional solutions, we can use the "port mirroring" function on the switch and we can "copy" traffic from the selected port / ports / vlan to another selected port where we connect the computer, eg with Wireshark software. In this way, we can intercept traffic at the interface speed, i.e. 1Gb / s or more (e.g. 10Gb / s), but at higher speeds there are significant requirements for devices that intercept and analyze the tested network traffic.
How can we deal in the "field" when we urgently need to examine the traffic between two devices in the LAN and we do not have a managed switch with the "mirror port" function, and we cannot install traffic analysis software on the devices (e.g. it is a router / printer pair / disk array / switch etc.).
Once a popular way was to use the outdated 10Mb / s hub, nowadays these types of devices are less available and limited bandwidth can be a problem.
We can use the 100Mb / s (fast Ethernet) passive tap method, which will allow intercepting network traffic between devices. It is a solution beyond all standards, which can even damage the equipment (in extreme cases). You can also "separate" yourself from the tap for greater security, e.g. with a fast Ethernet switch for ~ 40 PLN.
Use of the solution is at your own risk, but sometimes such a simple "tap" can be useful when troubleshooting network communication problems.
To prepare the "branch" I used two double 8P8C (RJ45) sockets,
to begin with, we connect the pins of one socket with the socket in the other module:
1 - 1 (TX +)
2 - 2 (TX-)
3 - 3 (RX +)
6 - 6 (RX-)

We get an "extension" that can work in the FastEthernet standard.
Then, in both modules, branch the transmission lines to the second socket. In one socket the transmitting pair (1,2), in the other socket a receiving pair (3,6). The pairs are branched to terminals 3,6 (RX +, RX-).
1 (TX +) - 3 (RX +)
2 (TX-) - 6 (RX-)
3 (RX +) - 3 (RX +)
6 (RX-) - 6 (RX-)

After closing the sockets, it is worth marking them so that the internal wiring diagram is clear to everyone:

Connect the device to the "Device" socket with a straight cable (patch), e.g. in the EIA / TIA T586B standard,
connect the existing cable connected to the interface of the device to the "Uplink" socket.
On Tap sockets we can intercept one-way transmissions "from the device" or "to the device". Connect a straight cable to the "Tap" socket and connect it to the network card in the computer with the Wireshark program installed. ifwe want to intercept the transmission in both directions at the same time, we need two network interfaces on the computer analyzing the traffic.
Due to the common AUTO MDI-MDIX (connection detection with a straight / patch or crossover / crossover cable), the transmission direction available on the Tap terminals is determined experimentally.
In my case, the traffic "from device to Uplink" was available on the "Tap" socket next to the "Uplink" socket, while the "Uplnik to device" traffic was available on the "Tap" socket next to the "Device" socket.
Passive Tap can be used only at your own risk (risk of damage / interference), in home conditions the "tap" may be useful to check the traffic between our home router and the operator's device with an Ethernet interface. You can check what communication is established by the home router and what traffic is coming to the WAN interface from the Internet. Attackers may try to use flaws in the software of cheap routers to build botnets or try, for example, to redirect us to a fake bank website, etc. Checking the router's communication with the Internet can detect anomalies. The device can be useful for education and experimenting with the LAN and for detecting problems with the devices launched (e.g. enc28j60).
What do you think about such a primitive way to analyze network traffic?




Comments
The fact that you showed that it works and this is mainly about (because the hardware itself is trivial) about the overall operation of such a system, i.e. also from the software side, etc., has a great... [Read more]
Can be quite miniaturized, for example, as you write using sockets from damaged equipment, you can also use only RJ45 plugs. I used the surface-mounted sockets because they had a full box, and it took... [Read more]
Since you need a computer with two network cards anyway, you just need to install "bridge" software on it to logically connect network cards with each other and record the transmission through one. No... [Read more]
Also a very nice idea for "wiretapping". But maybe this simple hardware tap can have some advantages in some situations as well. For example, that there is no risk of any interference with packets (some... [Read more]
All in all, this can be slightly reduced. Use a LAN tee like this one: https://obrazki.elektroda.pl/5696898200_1526275994_thumb.jpeg And build a cable https://obrazki.elektroda.pl/14195669... [Read more]
It's not really about that. Because it's not about splitting, but joining parallel to the line. But your suggestion of using such a tee is not bad. Because by properly preparing two such tees,... [Read more]
But that's what a tee does. Splits the signal into two of the same. So you can connect the source on one side, the receiver on the other and pull the tx and rx out of the third socket using the cable... [Read more]
Your diagram suggests something else. But you are right here that such a tee can be used as a tap without any modification, and from it a standard 1: 1 cable can go towards the eavesdropping computer.... [Read more]
I will also mention that to remove some of the problems, it was enough to analyze the packets from one tap sent by the device using a laptop with one network interface and Wireshark. On a computer with... [Read more]
And some more questions. How did you configure the IP address of these cards (because DHCP would not be able to find out)? I mean, is it possible to listen to packets from a completely different network... [Read more]
As for IP, they get APIPA without DHCP, but it is accidentally selected, it is better to configure fixed addresses, and set a filter in Wireshark that cuts out these IP addresses just in case. You can... [Read more]
I wonder if cheap switches with little memory can be forced to act as a HUB after flooding with false MAC addresses. They used to be attacked like that. [Read more]
I am of exactly the same opinion. In such cases, I use an additional USB card. I must admit that I was not even aware of the possibility of linking a card with only RX connected. I like the concept itself... [Read more]
Port mirroring is sometimes used in production, e.g. for recording calls in a callcenter, regardless of the Voip solutions used. RTP packets and signaling go to the recorder which composes the data into... [Read more]
It's a pity it's not that straightforward with Wi-Fi. During the reign of ESP8266 and ESP32, it would be very useful to me. [Read more]