Sometimes during deployment, it is necessary to capture network traffic between devices to resolve a problem to remove obstacles. In the case where one of the devices is a computer running software, it is often enough to have Wireshark software installed and check where the problem is. If we want to check the traffic between devices, it is necessary to intercept the transmission from the port of one of the devices.
In professional solutions, we can use the "port mirroring" function on the switch and we can "copy" traffic from the selected port / ports / vlan to another selected port where we connect the computer, eg with Wireshark software. In this way, we can intercept traffic at the interface speed, i.e. 1Gb / s or more (e.g. 10Gb / s), but at higher speeds there are significant requirements for devices that intercept and analyze the tested network traffic.
How can we deal in the "field" when we urgently need to examine the traffic between two devices in the LAN and we do not have a managed switch with the "mirror port" function, and we cannot install traffic analysis software on the devices (e.g. it is a router / printer pair / disk array / switch etc.).
Once a popular way was to use the outdated 10Mb / s hub, nowadays these types of devices are less available and limited bandwidth can be a problem.
We can use the 100Mb / s (fast Ethernet) passive tap method, which will allow intercepting network traffic between devices. It is a solution beyond all standards, which can even damage the equipment (in extreme cases). You can also "separate" yourself from the tap for greater security, e.g. with a fast Ethernet switch for ~ 40 PLN.
Use of the solution is at your own risk, but sometimes such a simple "tap" can be useful when troubleshooting network communication problems.
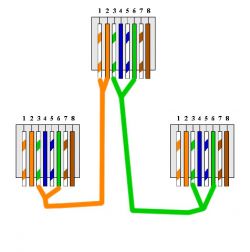
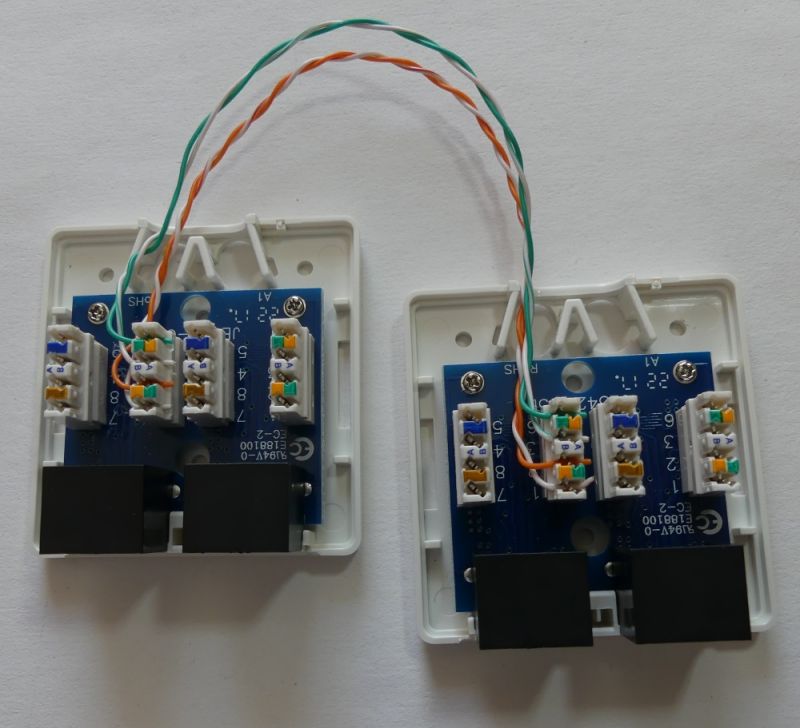
To prepare the "branch" I used two double 8P8C (RJ45) sockets,
to begin with, we connect the pins of one socket with the socket in the other module:
1 - 1 (TX +)
2 - 2 (TX-)
3 - 3 (RX +)
6 - 6 (RX-)
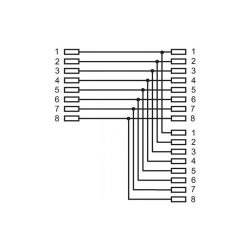
We get an "extension" that can work in the FastEthernet standard.
Then, in both modules, branch the transmission lines to the second socket. In one socket the transmitting pair (1,2), in the other socket a receiving pair (3,6). The pairs are branched to terminals 3,6 (RX +, RX-).
1 (TX +) - 3 (RX +)
2 (TX-) - 6 (RX-)
3 (RX +) - 3 (RX +)
6 (RX-) - 6 (RX-)
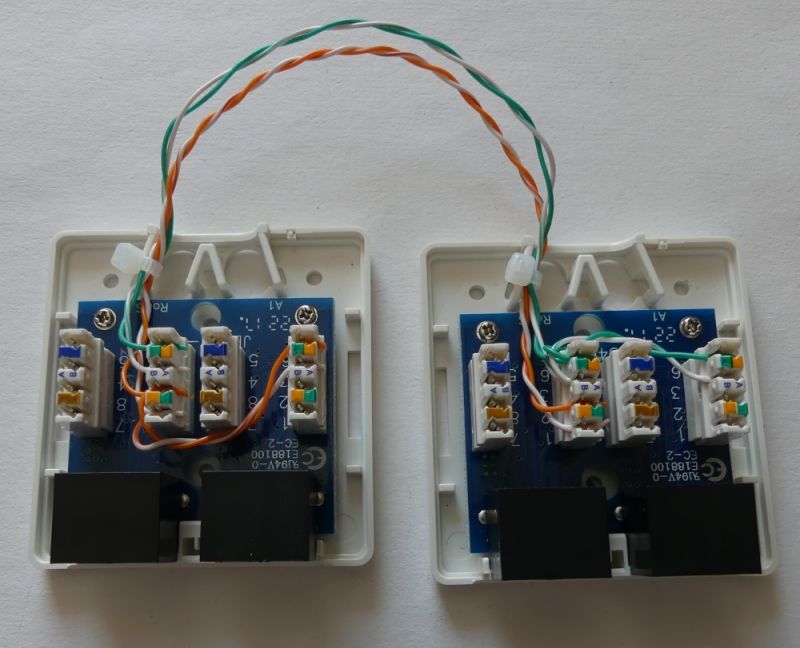
After closing the sockets, it is worth marking them so that the internal wiring diagram is clear to everyone:

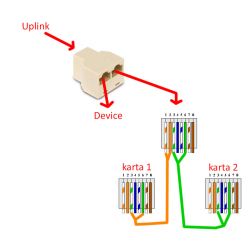
Connect the device to the "Device" socket with a straight cable (patch), e.g. in the EIA / TIA T586B standard,
connect the existing cable connected to the interface of the device to the "Uplink" socket.
On Tap sockets we can intercept one-way transmissions "from the device" or "to the device". Connect a straight cable to the "Tap" socket and connect it to the network card in the computer with the Wireshark program installed. ifwe want to intercept the transmission in both directions at the same time, we need two network interfaces on the computer analyzing the traffic.
Due to the common AUTO MDI-MDIX (connection detection with a straight / patch or crossover / crossover cable), the transmission direction available on the Tap terminals is determined experimentally.
In my case, the traffic "from device to Uplink" was available on the "Tap" socket next to the "Uplink" socket, while the "Uplnik to device" traffic was available on the "Tap" socket next to the "Device" socket.
Passive Tap can be used only at your own risk (risk of damage / interference), in home conditions the "tap" may be useful to check the traffic between our home router and the operator's device with an Ethernet interface. You can check what communication is established by the home router and what traffic is coming to the WAN interface from the Internet. Attackers may try to use flaws in the software of cheap routers to build botnets or try, for example, to redirect us to a fake bank website, etc. Checking the router's communication with the Internet can detect anomalies. The device can be useful for education and experimenting with the LAN and for detecting problems with the devices launched (e.g. enc28j60).
What do you think about such a primitive way to analyze network traffic?
In professional solutions, we can use the "port mirroring" function on the switch and we can "copy" traffic from the selected port / ports / vlan to another selected port where we connect the computer, eg with Wireshark software. In this way, we can intercept traffic at the interface speed, i.e. 1Gb / s or more (e.g. 10Gb / s), but at higher speeds there are significant requirements for devices that intercept and analyze the tested network traffic.
How can we deal in the "field" when we urgently need to examine the traffic between two devices in the LAN and we do not have a managed switch with the "mirror port" function, and we cannot install traffic analysis software on the devices (e.g. it is a router / printer pair / disk array / switch etc.).
Once a popular way was to use the outdated 10Mb / s hub, nowadays these types of devices are less available and limited bandwidth can be a problem.
We can use the 100Mb / s (fast Ethernet) passive tap method, which will allow intercepting network traffic between devices. It is a solution beyond all standards, which can even damage the equipment (in extreme cases). You can also "separate" yourself from the tap for greater security, e.g. with a fast Ethernet switch for ~ 40 PLN.
Use of the solution is at your own risk, but sometimes such a simple "tap" can be useful when troubleshooting network communication problems.
To prepare the "branch" I used two double 8P8C (RJ45) sockets,
to begin with, we connect the pins of one socket with the socket in the other module:
1 - 1 (TX +)
2 - 2 (TX-)
3 - 3 (RX +)
6 - 6 (RX-)

We get an "extension" that can work in the FastEthernet standard.
Then, in both modules, branch the transmission lines to the second socket. In one socket the transmitting pair (1,2), in the other socket a receiving pair (3,6). The pairs are branched to terminals 3,6 (RX +, RX-).
1 (TX +) - 3 (RX +)
2 (TX-) - 6 (RX-)
3 (RX +) - 3 (RX +)
6 (RX-) - 6 (RX-)

After closing the sockets, it is worth marking them so that the internal wiring diagram is clear to everyone:

Connect the device to the "Device" socket with a straight cable (patch), e.g. in the EIA / TIA T586B standard,
connect the existing cable connected to the interface of the device to the "Uplink" socket.
On Tap sockets we can intercept one-way transmissions "from the device" or "to the device". Connect a straight cable to the "Tap" socket and connect it to the network card in the computer with the Wireshark program installed. ifwe want to intercept the transmission in both directions at the same time, we need two network interfaces on the computer analyzing the traffic.
Due to the common AUTO MDI-MDIX (connection detection with a straight / patch or crossover / crossover cable), the transmission direction available on the Tap terminals is determined experimentally.
In my case, the traffic "from device to Uplink" was available on the "Tap" socket next to the "Uplink" socket, while the "Uplnik to device" traffic was available on the "Tap" socket next to the "Device" socket.
Passive Tap can be used only at your own risk (risk of damage / interference), in home conditions the "tap" may be useful to check the traffic between our home router and the operator's device with an Ethernet interface. You can check what communication is established by the home router and what traffic is coming to the WAN interface from the Internet. Attackers may try to use flaws in the software of cheap routers to build botnets or try, for example, to redirect us to a fake bank website, etc. Checking the router's communication with the Internet can detect anomalies. The device can be useful for education and experimenting with the LAN and for detecting problems with the devices launched (e.g. enc28j60).
What do you think about such a primitive way to analyze network traffic?