Hello,
I wanted to share my observations regarding the structure / structure of the firmware
router: Huawei B593s-22 . I have succeeded in this play by accident, and I have little free time
I decided to publish all the information on how to do it on this forum.
!!! For the first time on the Internet - you won't find this information anywhere else !!!
This is of course the ability to extract files and directory structure from
"firmware.bin" designed for Huawei LTE CPE B593s-22 !!!
I think that there will be a few people on the elektroda.pl forum who can use this information
find a way to freely modify the firmware of this device,
and to extract the password encryption algorithm - what would be possible to log into the SSH console.
It is interesting as it would allow us to restore, for example, "POLISH" language for the last one
FW: V200R001B270D10SP00C00 (probably due to Polish operators it was " / * commented * / ".
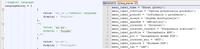
I will not even mention the menu for selecting the frequency of the 3g / 4g modem.
As for the firmware itself, I have a few questions, I hope someone knows the answers, or has an unnecessary B593s-22 router for testing and knows how to use the programmer:
- FW consists of 9 parts - would it be successful to try to upload one (which is a partition image, e.g.: WebUI)?
- Do we skip Android for VxWorks when updating with the tool: "B593s-22 Multicast upgrade tool"?
- What is the probability that FW (update.app) is "signed" for Android, and how is it signed: as a whole or each of the images
in turn, or maybe only the Android partition is signed?
- How is it possible that replacing the firmware version works if this value is involved in counting the checksum of the header section?
- How is it possible that the replacement of the FW number in the header section ending with 2 digits into 3 digits "broke" the equipment?
Attached is a file in [pdf] format with the entire extraction procedure and a few details about the structure of this firmware.
In the tutorial I used a free "hex" editor HxD .
* if you have any comments or noticed mistakes in the publication, write and I will introduce corrections
(if you find spelling mistakes, write to "priv" - save me the embarrassment
 )
)
I invite you to read the materials - GREETINGS :spoko:
I wanted to share my observations regarding the structure / structure of the firmware
router: Huawei B593s-22 . I have succeeded in this play by accident, and I have little free time
I decided to publish all the information on how to do it on this forum.
!!! For the first time on the Internet - you won't find this information anywhere else !!!
This is of course the ability to extract files and directory structure from
"firmware.bin" designed for Huawei LTE CPE B593s-22 !!!
I think that there will be a few people on the elektroda.pl forum who can use this information
find a way to freely modify the firmware of this device,
and to extract the password encryption algorithm - what would be possible to log into the SSH console.
It is interesting as it would allow us to restore, for example, "POLISH" language for the last one
FW: V200R001B270D10SP00C00 (probably due to Polish operators it was " / * commented * / ".

I will not even mention the menu for selecting the frequency of the 3g / 4g modem.
As for the firmware itself, I have a few questions, I hope someone knows the answers, or has an unnecessary B593s-22 router for testing and knows how to use the programmer:
- FW consists of 9 parts - would it be successful to try to upload one (which is a partition image, e.g.: WebUI)?
- Do we skip Android for VxWorks when updating with the tool: "B593s-22 Multicast upgrade tool"?
- What is the probability that FW (update.app) is "signed" for Android, and how is it signed: as a whole or each of the images
in turn, or maybe only the Android partition is signed?
- How is it possible that replacing the firmware version works if this value is involved in counting the checksum of the header section?
- How is it possible that the replacement of the FW number in the header section ending with 2 digits into 3 digits "broke" the equipment?
Attached is a file in [pdf] format with the entire extraction procedure and a few details about the structure of this firmware.
In the tutorial I used a free "hex" editor HxD .
* if you have any comments or noticed mistakes in the publication, write and I will introduce corrections
(if you find spelling mistakes, write to "priv" - save me the embarrassment
I invite you to read the materials - GREETINGS :spoko:
Moderated By jimasek:Online Safety Notice:
Please note that the sources provided by the colleague of the author of the post are not authorized by the manufacturer in any way, so downloading, changing and installing such software is at your own risk.


