Hello to everyone interested in the topic of modification, improvement of operation and strengthening of work safety on the Huawei b593-s22 router.
A few Off-topic sentences:
I am developing a neat application to modify both the firmware and remote management of this router, however it is a big project, and as I am a hobbyist, I cannot devote as much time to it as I would like. Now spring is coming, so I will spend the next month on the plot (300m2 and "Americans" are already waiting). So I decided to describe the procedure of decoding the configuration file and device access passwords for the safety of network users.
To decode the file: downloadconfigfile.conf you will need: OpenSSL .
For deciphering passwords, I recommend the free one: BP-Tools
I suggest BP-Tools because OpenSSL was causing problems on my computer (and it couldn't open / find the file, and it had to create a configuration file for him), and besides, it's a command-line application.
Let's get to the point:
To decode the configuration file, the following command is enough:
To encrypt:
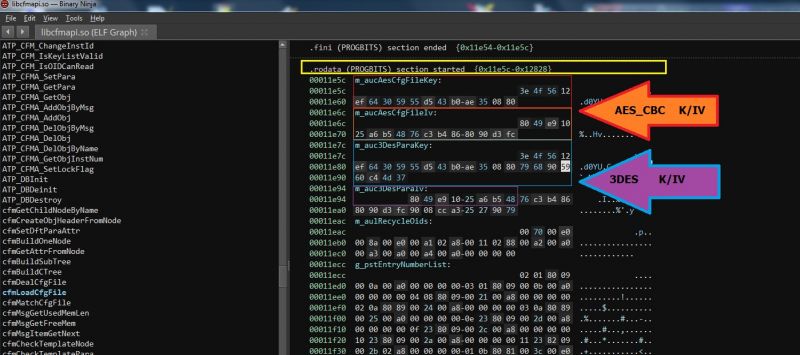
As you can easily guess, the algorithm is AES 128 CBC Key: 3E4F5612EF64305955D543B0AE350880; IV: 8049E91025A6B54876C3B4868090D3FC.
However, you have to be careful about the file size - it must be a multiple of 16 bytes -> Huawei uses an unconventional method for AES CBC, namely ZERO "padding" (when you change the file size, you will need a HEX editor to add a few "00" to the end of the file - so that the size in bytes divided by 16 does not give the remainder).
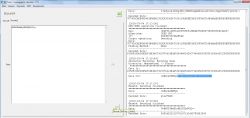
The decrypted configuration file is in * .xml format, so any text editor will be needed to edit it ... The above "print screen" shows a fragment of this file with default passwords to the router's WebGUI - for the "admin" account the encrypted password is here: f3nGyuud1GOwq4E1LtMDbWcQgRAK3uxuUf + Ezxi0qq6OXeW9 / qX22A == .
Therefore, we proceed to decryption:
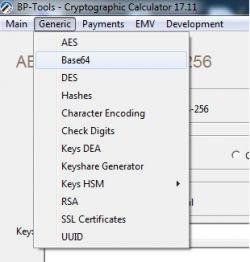
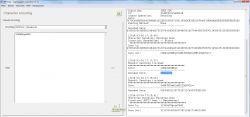
1. Select 'Base64' from the "Generic" menu of BP-Tools (Cryptographic Calculator):
and we decode our password to hexadecimal form:
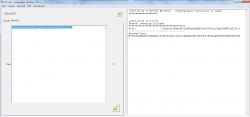
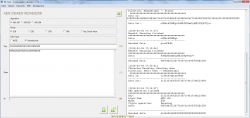
2. From the "Generic" menu of the program, select 'DES' ('3DES', 'CBC', 'Heksadecimal', 'Padding: None'). The decryption key is: K: 3E4F5612EF64305955D543B0AE3508807968905960C44D37 ; IV: 8049E91025A6B548 . The HEX string from the previous operation will be decrypted, so: 7F79C6CAEB9DD463B0AB81352ED3036D671081100ADEEC6E51FF84CF18B4AAAE8E5DE5BDFEA5F6D8:
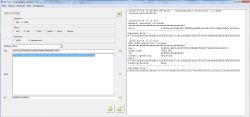
3. From the "Generic" menu of the program, select 'Character encoding' -> 'Heksadecimal-> binary' and en-encode the data resulting from the "3DES" decryption, so: 63585268636B5A534E4667363976424E4A53494865426C7948456C58395134500640013D3D
4. The resulting string (Base64) should be DIVIDED into 2 parts -> in the first part, use 12 (!!!) characters: cXRhckZSNFg6; in the second part the remaining characters: 9vBNJSIHeBlyHElX9Q4VCQ ==.
From the 'Character encoding' menu, choose 'ASCII Text -> Heksadecimal' and en-encode characters separately for two parts:
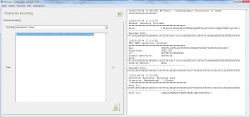
5. Staying in 'Character encoding' - 'ASCII Text -> Heksadecimal' in the 'Data' field, enter the numbers from 1 to 8 at the end of which we add the en-encoded characters from the first part (8 characters, ':' skipping) of the previous point, so in this case the whole is: 12345678qtarFR4X:
6. Having enough data, select 'AES' ('AES-128', 'ECB', 'Hexadecimal') from the "Generic" menu of the program. The key here is the hexadecimal sequence from the previous point (12345678qtarFR4X), so: 31323334353637387174617246523458. The hexadecimal string from the second part will be deciphered (see point 4.9vBNJSIHeBlyHElX9Q4VCQ ==), that is: F6F04D2522077819721C4957F50E1509
7. At the end, from the "Generic" menu of the program, select 'Character encoding' -> 'Heksadecimal-> binary' and en-encode the obtained value, i.e .: 61646D696E0000000000000000000000 to ASCII characters and this is how we obtain the password (in this particular case) admin ( "00" is omitted !!!)
If you want to change the valid password on the router, proceed in the reverse order, except that:
-you need to create a unique combination of eight characters (lowercase and uppercase letters + numbers), it will be the second half of the AES ECB encryption key (the first half is 12345678 and it should stay that way),
-conceive / generate a unique password (max 16 characters - in the case of a short password to hexadecimal form, complete "00" with zeros up to a total length of 16 bytes),
-in the encryption stage '3DES' -> "Data Input" = 'ASCII' -> "Padding Method" = 'Zeros',
- if everything goes well, the new password will be 56 characters long and should be overwritten in the right place in the configuration file.
To this topic I attach a log of the entire operation (the log also includes reverse steps, i.e. password encryption) ... it will definitely be helpful.
I encourage forum users skilled in creating batch files, programs in high-level languages to embrace the topic for less informed users.
I myself am a supporter of asm, at most ANSI C, and my project is quite extensive and a few more months to master it will be gone.
PS
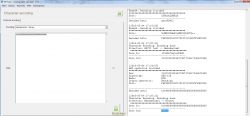
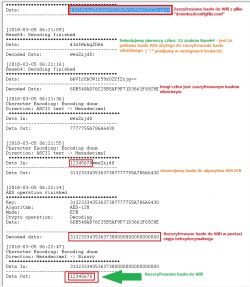
Only the WebGUI and CLI passwords are encrypted simultaneously with the 3DES and AES_ECB algorithms ... The rest of the passwords only require the use of the AES_ECB -> "log" algorithm from decoding the sample Wifi password below:
Regards.
ATTENTION !!!
If you are the owner of this device, you should IMMEDIATELY change the CLI access passwords in your device - Huawei uses the same default passwords for the same series of devices - it is a very DANGEROUS and reckless approach of the manufacturer, exposing you to unauthorized access to your network !!!
If you are the owner of this device, you should IMMEDIATELY change the CLI access passwords in your device - Huawei uses the same default passwords for the same series of devices - it is a very DANGEROUS and reckless approach of the manufacturer, exposing you to unauthorized access to your network !!!
A few Off-topic sentences:
I am developing a neat application to modify both the firmware and remote management of this router, however it is a big project, and as I am a hobbyist, I cannot devote as much time to it as I would like. Now spring is coming, so I will spend the next month on the plot (300m2 and "Americans" are already waiting). So I decided to describe the procedure of decoding the configuration file and device access passwords for the safety of network users.
To decode the file: downloadconfigfile.conf you will need: OpenSSL .
For deciphering passwords, I recommend the free one: BP-Tools
I suggest BP-Tools because OpenSSL was causing problems on my computer (and it couldn't open / find the file, and it had to create a configuration file for him), and besides, it's a command-line application.
Let's get to the point:
To decode the configuration file, the following command is enough:
openssl enc -d -aes-128-cbc -in downloadconfigfile.conf -out downloadconfigfile.xml -K 3E4F5612EF64305955D543B0AE350880 -iv 8049E91025A6B54876C3B4868090D3FC -November
To encrypt:
openssl enc -e -aes-128-cbc -in downloadconfigfile.xml -out downloadconfigfile.conf -K 3E4F5612EF64305955D543B0AE350880 -iv 8049E91025A6B54876C3B4868090D3FC -November
As you can easily guess, the algorithm is AES 128 CBC Key: 3E4F5612EF64305955D543B0AE350880; IV: 8049E91025A6B54876C3B4868090D3FC.
However, you have to be careful about the file size - it must be a multiple of 16 bytes -> Huawei uses an unconventional method for AES CBC, namely ZERO "padding" (when you change the file size, you will need a HEX editor to add a few "00" to the end of the file - so that the size in bytes divided by 16 does not give the remainder).
================================================== =
Decrypting passwords from the configuration file:
The decrypted configuration file is in * .xml format, so any text editor will be needed to edit it ... The above "print screen" shows a fragment of this file with default passwords to the router's WebGUI - for the "admin" account the encrypted password is here: f3nGyuud1GOwq4E1LtMDbWcQgRAK3uxuUf + Ezxi0qq6OXeW9 / qX22A == .
Therefore, we proceed to decryption:
1. Select 'Base64' from the "Generic" menu of BP-Tools (Cryptographic Calculator):
and we decode our password to hexadecimal form:
2. From the "Generic" menu of the program, select 'DES' ('3DES', 'CBC', 'Heksadecimal', 'Padding: None'). The decryption key is: K: 3E4F5612EF64305955D543B0AE3508807968905960C44D37 ; IV: 8049E91025A6B548 . The HEX string from the previous operation will be decrypted, so: 7F79C6CAEB9DD463B0AB81352ED3036D671081100ADEEC6E51FF84CF18B4AAAE8E5DE5BDFEA5F6D8:
3. From the "Generic" menu of the program, select 'Character encoding' -> 'Heksadecimal-> binary' and en-encode the data resulting from the "3DES" decryption, so: 63585268636B5A534E4667363976424E4A53494865426C7948456C58395134500640013D3D
4. The resulting string (Base64) should be DIVIDED into 2 parts -> in the first part, use 12 (!!!) characters: cXRhckZSNFg6; in the second part the remaining characters: 9vBNJSIHeBlyHElX9Q4VCQ ==.
From the 'Character encoding' menu, choose 'ASCII Text -> Heksadecimal' and en-encode characters separately for two parts:
5. Staying in 'Character encoding' - 'ASCII Text -> Heksadecimal' in the 'Data' field, enter the numbers from 1 to 8 at the end of which we add the en-encoded characters from the first part (8 characters, ':' skipping) of the previous point, so in this case the whole is: 12345678qtarFR4X:
6. Having enough data, select 'AES' ('AES-128', 'ECB', 'Hexadecimal') from the "Generic" menu of the program. The key here is the hexadecimal sequence from the previous point (12345678qtarFR4X), so: 31323334353637387174617246523458. The hexadecimal string from the second part will be deciphered (see point 4.9vBNJSIHeBlyHElX9Q4VCQ ==), that is: F6F04D2522077819721C4957F50E1509
7. At the end, from the "Generic" menu of the program, select 'Character encoding' -> 'Heksadecimal-> binary' and en-encode the obtained value, i.e .: 61646D696E0000000000000000000000 to ASCII characters and this is how we obtain the password (in this particular case) admin ( "00" is omitted !!!)
================================================== =
If you want to change the valid password on the router, proceed in the reverse order, except that:
-you need to create a unique combination of eight characters (lowercase and uppercase letters + numbers), it will be the second half of the AES ECB encryption key (the first half is 12345678 and it should stay that way),
-conceive / generate a unique password (max 16 characters - in the case of a short password to hexadecimal form, complete "00" with zeros up to a total length of 16 bytes),
-in the encryption stage '3DES' -> "Data Input" = 'ASCII' -> "Padding Method" = 'Zeros',
- if everything goes well, the new password will be 56 characters long and should be overwritten in the right place in the configuration file.
To this topic I attach a log of the entire operation (the log also includes reverse steps, i.e. password encryption) ... it will definitely be helpful.
I encourage forum users skilled in creating batch files, programs in high-level languages to embrace the topic for less informed users.
I myself am a supporter of asm, at most ANSI C, and my project is quite extensive and a few more months to master it will be gone.
ATTENTION !!!
Knowing the router's CLI password, you can configure the device via "ATP / shell / AT commands", but I do not recommend it, as it may damage the operating system of the device - such a device will be difficult to repair, if it can be repaired at all. !!!
Knowing the router's CLI password, you can configure the device via "ATP / shell / AT commands", but I do not recommend it, as it may damage the operating system of the device - such a device will be difficult to repair, if it can be repaired at all. !!!
PS
Only the WebGUI and CLI passwords are encrypted simultaneously with the 3DES and AES_ECB algorithms ... The rest of the passwords only require the use of the AES_ECB -> "log" algorithm from decoding the sample Wifi password below:
Regards.



 .
.