Welcome!
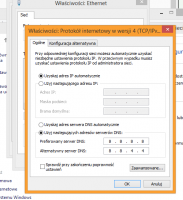
The problem is that the auction description on the Allegro appears for a second, the page reloads and ads appear, and the description disappears. I have already seen such a problem here in the forum, I did everything in turn (scan malwarebytes anti-malware, adwcleaner, cc cleaner, eset) - generally found something there and removed it, but it did not change anything. Then I changed the DNS on windows and router to 8.8.8.8 and 8.8.4.4 - still nothing.
Unfortunately, due to another router "It is particularly important to block access to the panel: http://www.tp-link.com.pl/article/?faqid=568" I do not have the options there as in the article in the access control tab I checked "Enable Internet Access Control". I also did ipconfig / flushdns in cmd.
I also attach logs from FRST.
What else can I do..?
The problem is that the auction description on the Allegro appears for a second, the page reloads and ads appear, and the description disappears. I have already seen such a problem here in the forum, I did everything in turn (scan malwarebytes anti-malware, adwcleaner, cc cleaner, eset) - generally found something there and removed it, but it did not change anything. Then I changed the DNS on windows and router to 8.8.8.8 and 8.8.4.4 - still nothing.
Unfortunately, due to another router "It is particularly important to block access to the panel: http://www.tp-link.com.pl/article/?faqid=568" I do not have the options there as in the article in the access control tab I checked "Enable Internet Access Control". I also did ipconfig / flushdns in cmd.
I also attach logs from FRST.
What else can I do..?