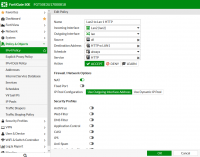
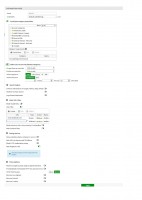
In the category tree you can add a subcategory in local categories, for example "Blocked", to which you can add blocked pages. These categories can then be used in the same way as the predefined ones in different web filter profiles. In your profile, you block the entire category once and then drag new pages to it.
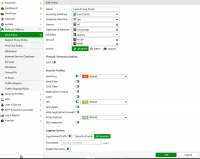
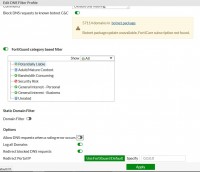
Simple URL block works poorly, at least in forti 5.0 and 5.2. If you want to block facebook just like in the screenshot, it is best to look at the application blocking configuration - there you can even set that on other pages you will see fb components (e.g. sliders, paws, etc.), but you cannot enter fb itself. This is quite a good option, because cutting out completely spoils some other websites (e.g. a frame with info about the blockade pops up in the place of the slider).
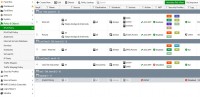
Breaking policies as you have in the screen is a bit pointless, as long as there is little, it can and looks nice, but if you started creating, for example, network / service access schedules, or various configurations for user groups, you will not get it later, because each entry it will split into several more. If the policies do not differ in the settings of av profiles, web filter, ips, etc., it is better to leave it as one entry. Note that forti is quite clever and if you turn on the email filter on a given policy entry, it doesn't mean that this filter works for all services - it will only work for emails automatically (this is defined in the system configuration). The same goes for other filters, antivirus, etc.
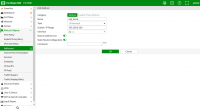
As for the DNS filter not working, it is possible you have something wrongly set up in the configuration of the system itself and eg DNS fortiguarda are unreachable.