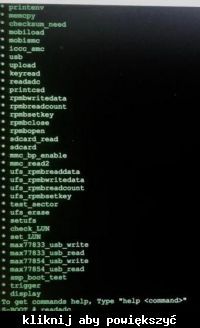
I have the phone mentioned above and the task of recovering data from it (the most important contacts). The problem is that the phone has a completely smashed screen, nor does it display or respond to touch. The good news is that the phone has usb debugging enabled. The problem is that when I connect it and try to do anything with adb commands, it turns out that on the phone you need to allow the computer to use debugging. Is this something you can do?