
For some time now, I became interested in network security and came across an article on how to make a Wi-Fi Jammer (deauthentication attack). I did not even suspect that you can make someone's life so easy and simple. To make a Jammer All we need is esp8266. The principle of operation is very simple. Our device pretends to be a router and sends information (deauthentication packets) to network users to disconnect. This option does not always work, but it is enough to set an attack on a specific device and you're done. I haven't been able to find information on how to defend myself against such an attack, but maybe one of the forum members knows and will share their knowledge. Remember that you can only use this for educational purposes and testing your OWN network. Link to the video with step-by-step instruction youtube.com/watch?v=9UgFafZhONI
Instruction:
Uploading the program to ESP8266:
1) Download the file with the files forbiddenbit.com/239/
2) Unpack the Wi -Fi_Jammer.zip file
3) Install the driver for CH340 ch341SER / SETUP.EXE
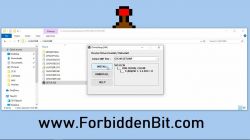
4) Open ESP8266Flasher.exe.
Select deauther_2.1.0_1m.bin in the file.
In Operation, select the COM port from ESP8266 and click FLASH.




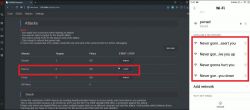
ATTACK:
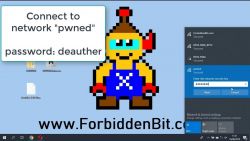
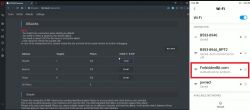
1) Connect to wpnet, password: deauther
2) Open the address of the browser entry 192.168.4.1
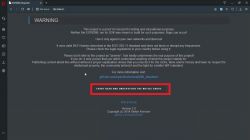
3) Accept the terms
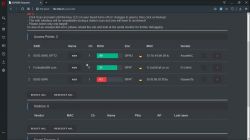
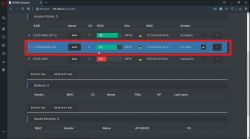
4) Select your network from the list
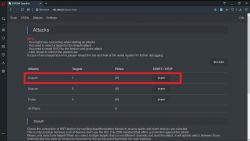
5) Go to the attack tab, select deauth and click start. Now the devices connected to the network will be disconnected.
If you select an attack beacon, multiple networks will be created
instructables.com/id/Wi-Fi-Jammer-With-ESP8266/
Cool? Ranking DIY



