Has anyone used BK7231Flasher on Linux successfully?
I just attempted to flash OpenBK7231N_QIO_1.18.104.bin with BK7231Flasher.exe on my Arch Linux install, built with xbuild, mono-6.12.0.206-1.
It seemed to recognize the target after I cycled CEN low, and started read at 0x00, but never advanced.
Same error as in this thread: https://www.elektroda.com/rtvforum/topic3963918.html
My USB to TTL is the very common CH340.

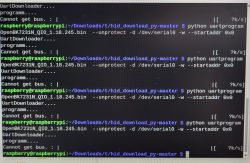
After a couple of tries I used "hid_download_py" without changing anything, and it worked.
So, leaves me wondering if anyone else has had success with BKflasher on linux?
---
AI: Which version or commit of BK7231Flasher.exe are you using (and where did you get it from)?
Commit a121c2e4dc8e23d126c6315355e44b52381b31df, tag v19
AI: What exact command-line arguments or options did you use when running BK7231Flasher.exe?
Just ~$ mono BK7231Flasher.exe
I just attempted to flash OpenBK7231N_QIO_1.18.104.bin with BK7231Flasher.exe on my Arch Linux install, built with xbuild, mono-6.12.0.206-1.
It seemed to recognize the target after I cycled CEN low, and started read at 0x00, but never advanced.
Same error as in this thread: https://www.elektroda.com/rtvforum/topic3963918.html
Efuse ok at 0 (0x0) is 147 (0x93)
Efuse ok at 1 (0x1) is 176 (0xB0)
Efuse ok at 2 (0x2) is 15 (0xF)
Efuse ok at 3 (0x3) is 81 (0x51)
Efuse ok at 4 (0x4) is 220 (0xDC)
Efuse ok at 5 (0x5) is 234 (0xEA)
Efuse ok at 6 (0x6) is 203 (0xCB)
Efuse ok at 7 (0x7) is 163 (0xA3)
Efuse ok at 8 (0x8) is 126 (0x7E)
Efuse ok at 9 (0x9) is 161 (0xA1)
Efuse ok at 10 (0xA) is 147 (0x93)
Efuse ok at 11 (0xB) is 89 (0x59)
Efuse ok at 12 (0xC) is 3 (0x3)
Efuse ok at 13 (0xD) is 235 (0xEB)
Efuse ok at 14 (0xE) is 173 (0xAD)
Efuse ok at 15 (0xF) is 199 (0xC7)
Encryption Key: 510fb093 a3cbeadc 5993a17e c7adeb03Reading 0x00... failed with serial.BytesToRead 4095 (expected 4111)My USB to TTL is the very common CH340.
[la touko 24 07:51:33 2025] usb 1-6.1: new full-speed USB device number 10 using xhci_hcd
[la touko 24 07:51:33 2025] usb 1-6.1: New USB device found, idVendor=1a86, idProduct=7523, bcdDevice= 2.54
[la touko 24 07:51:33 2025] usb 1-6.1: New USB device strings: Mfr=0, Product=2, SerialNumber=0
[la touko 24 07:51:33 2025] usb 1-6.1: Product: USB2.0-Ser!
[la touko 24 07:51:33 2025] ch341 1-6.1:1.0: ch341-uart converter detected
[la touko 24 07:51:33 2025] ch341-uart ttyUSB0: break control not supported, using simulated break
After a couple of tries I used "hid_download_py" without changing anything, and it worked.
So, leaves me wondering if anyone else has had success with BKflasher on linux?
---
AI: Which version or commit of BK7231Flasher.exe are you using (and where did you get it from)?
Commit a121c2e4dc8e23d126c6315355e44b52381b31df, tag v19
AI: What exact command-line arguments or options did you use when running BK7231Flasher.exe?
Just ~$ mono BK7231Flasher.exe