On 6 March 2025, Tarlogic published a press release entitled 'Tarlogic detects backdoor in mass-produced ESP32 chip that could infect millions of IoT devices'. This information was later picked up by the BleepingComputer website and circulated via Slashdot, Google News. In short, 'researchers' announced a week ago that they had detected a backdoor in ESP32 from Chinese manufacturer Espressif, published an article which first had a title suggesting a security vulnerability. Quite quickly, the manufacturer issued a statement and then documented in detail . It turned out that the so-called 'back door' was simply.... undocumented API. This is in fact a common design pattern also found in Bluetooth chips from other manufacturers such as Broadcom, Cypress and Texas Instruments. Manufacturer-specific commands in Bluetooth are in fact a 'private API', and a company's decision not to document this API does not constitute a 'backdoor'. The researchers' article quickly changed its title to 'Undocumented commands'  .
.
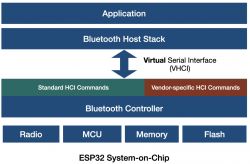
Bluetooth has an architectural layer known as the Host Controller Interface (HCI). In architectures such as laptops and phones, the main processor and operating system is the "Host" and the Bluetooth chip is the "Controller". HCI is the interface between the Host and the Controller. When the Host wants to search for nearby available BT devices or connect to one of them, it sends a Command through the HCI to the Controller.
The Bluetooth Core specification defines a number of HCI commands, but also reserves a command space for 'Manufacturer Specific Commands' (VSC). These are commands that the manufacturer can use to manage the Controller. They can include such things as updating the Controller software, obtaining useful information (e.g. chip temperature), performing chip-specific actions (e.g. setting transmission power), etc. VSCs are typically used by manufacturers through their proprietary software.
What does the study describe?
The study describes the reverse engineering of the ESP32 ROM, using a copy that Espressif makes available on GitHub. The researchers analyse the VSC and find instances of reading and writing RAM and flash, as well as sending certain types of low-level packets that cannot normally be sent from the Host.
Importantly, the research slides themselves do not claim that this is a backdoor. Only the press release suggests this. The slides merely indicate that there are hidden/undocumented commands.
Espressif has partially documented its VSC, as have other Bluetooth chip manufacturers, and has included the ability to read and write the chip's memory, as have other Bluetooth chip manufacturers.
The author concludes that Tarlogic's press release spreads fear, uncertainty and doubt (FUD) in order to attract attention. And the BleepingComputer article and its messages on platforms such as Slashdot, focusing on the fact that Espressif is a Chinese supplier.
Is this feature a security vulnerability?
It depends.
In general, the author considers the use of VSCs that give the ability to read and write memory, flash or registers to be a bad security design. It is a bad design for Espressif, just as it is for Broadcom, Texas Instruments and any other vendor that uses it.
This issue is now tracked as CVE-2025-27840 .
Espressif itself states that there is no real, known security risk that these undocumented commands could pose. Despite this, Espressif has decided to take the following action:
- Espressif will provide a patch that removes access to these HCI debug commands through a software update for currently supported versions of ESP-IDF.
- Espressif will document all vendor-specific HCI commands to provide transparency of the functionality available at the HCI layer.
The ESP32-C, ESP32-S and ESP32-H series chips are not affected as their Bluetooth controllers do not support these commands.
What do hack news users think about this?
https://news.ycombinator.com/item?id=43330331
1. users express satisfaction that Espressif has chosen to be more transparent, rather than further restricting access to features.
2. Although the company initially gained popularity in the DIY community, their chips are now present in billions of edge devices and professional products.
3. ESP chips gained popularity during the pandemic when they were the only Wi-Fi/BT modules available in a market suffering from a semiconductor shortage.
4) Some users express concern that removing access to debug commands will hinder researchers and those interested in experimenting with these features.
5) Many commenters emphasise that it was exaggerated and irresponsible to present this issue as a 'back door'.
6 The general opinion is that this is not a real security issue, as an attacker would already have to have full access to the device to exploit these commands.
7. users recommend disabling Bluetooth on devices when it is not needed, which is in line with some CE regulations.
8. some believe that these undocumented features are standard industry practice and not a deliberate security threat.
The following was used to write the article:
https://darkmentor.com/blog/esp32_non-backdoor/
https://developer.espressif.com/blog/2025/03/esp32-bluetooth-clearing-the-air/
official release:
https://www.espressif.com/en/news/Response_ESP32_Bluetooth
I don't know about you, but I am impressed by Espressif's explanation and handling of the matter, they have gained more trust with me.
.
Comments summarised using Claude 3.7
Bluetooth has an architectural layer known as the Host Controller Interface (HCI). In architectures such as laptops and phones, the main processor and operating system is the "Host" and the Bluetooth chip is the "Controller". HCI is the interface between the Host and the Controller. When the Host wants to search for nearby available BT devices or connect to one of them, it sends a Command through the HCI to the Controller.
The Bluetooth Core specification defines a number of HCI commands, but also reserves a command space for 'Manufacturer Specific Commands' (VSC). These are commands that the manufacturer can use to manage the Controller. They can include such things as updating the Controller software, obtaining useful information (e.g. chip temperature), performing chip-specific actions (e.g. setting transmission power), etc. VSCs are typically used by manufacturers through their proprietary software.
What does the study describe?
The study describes the reverse engineering of the ESP32 ROM, using a copy that Espressif makes available on GitHub. The researchers analyse the VSC and find instances of reading and writing RAM and flash, as well as sending certain types of low-level packets that cannot normally be sent from the Host.
Importantly, the research slides themselves do not claim that this is a backdoor. Only the press release suggests this. The slides merely indicate that there are hidden/undocumented commands.
Espressif has partially documented its VSC, as have other Bluetooth chip manufacturers, and has included the ability to read and write the chip's memory, as have other Bluetooth chip manufacturers.
The author concludes that Tarlogic's press release spreads fear, uncertainty and doubt (FUD) in order to attract attention. And the BleepingComputer article and its messages on platforms such as Slashdot, focusing on the fact that Espressif is a Chinese supplier.
Is this feature a security vulnerability?
It depends.
In general, the author considers the use of VSCs that give the ability to read and write memory, flash or registers to be a bad security design. It is a bad design for Espressif, just as it is for Broadcom, Texas Instruments and any other vendor that uses it.
This issue is now tracked as CVE-2025-27840 .
Espressif itself states that there is no real, known security risk that these undocumented commands could pose. Despite this, Espressif has decided to take the following action:
- Espressif will provide a patch that removes access to these HCI debug commands through a software update for currently supported versions of ESP-IDF.
- Espressif will document all vendor-specific HCI commands to provide transparency of the functionality available at the HCI layer.
The ESP32-C, ESP32-S and ESP32-H series chips are not affected as their Bluetooth controllers do not support these commands.
What do hack news users think about this?
https://news.ycombinator.com/item?id=43330331
1. users express satisfaction that Espressif has chosen to be more transparent, rather than further restricting access to features.
2. Although the company initially gained popularity in the DIY community, their chips are now present in billions of edge devices and professional products.
3. ESP chips gained popularity during the pandemic when they were the only Wi-Fi/BT modules available in a market suffering from a semiconductor shortage.
4) Some users express concern that removing access to debug commands will hinder researchers and those interested in experimenting with these features.
5) Many commenters emphasise that it was exaggerated and irresponsible to present this issue as a 'back door'.
6 The general opinion is that this is not a real security issue, as an attacker would already have to have full access to the device to exploit these commands.
7. users recommend disabling Bluetooth on devices when it is not needed, which is in line with some CE regulations.
8. some believe that these undocumented features are standard industry practice and not a deliberate security threat.
The following was used to write the article:
https://darkmentor.com/blog/esp32_non-backdoor/
https://developer.espressif.com/blog/2025/03/esp32-bluetooth-clearing-the-air/
official release:
https://www.espressif.com/en/news/Response_ESP32_Bluetooth
I don't know about you, but I am impressed by Espressif's explanation and handling of the matter, they have gained more trust with me.
.
Comments summarised using Claude 3.7