Good morning!
Below I will present a brief technical description of the device itself and steps to free it from the manufacturer`s cloud without changing the firmware.

I bought the camera on a well-known auction site, it cost PLN 75 then, now it costs PLN 85.
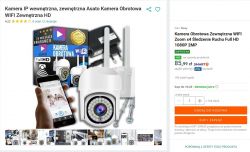
TECHNICAL DESCRIPTION
Technical data according to the seller:
To install the camera, use the appropriate application (Aview) available for mobile devices.
Using it, we can connect it to the home WiFi network (STA) or use it in AP mode (connect to its hotspot).
To be able to connect to the camera remotely, we need to log it into the Alibaba cloud (CN) and everything that happens to it goes through their servers (!).
This creates a huge danger because we have a foreign device in our LAN with full access to the network, and I don`t need to explain what can be done in such a configuration..
The device can be easily disassembled, 3 screws connect the balls to the camera and the whole thing is suspended on the ears of the rotating mechanism (1 screw).
I had to disassemble it to replace the power cable - the original one was a 15 cm cable with a plug, I replaced it with a longer one.
I don`t want to go into the details of the construction - one note, the rotation mechanisms do not have information about the position, everything is based on the number of rotation steps,
at startup, full-range calibration must occur in both axes.
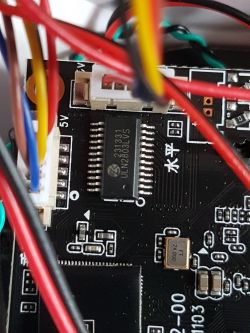
Below are some photos of the interior.
Main board:

WiFi module:

Motor controls and their appearance:


LISTENING TO THE PROTOCOL
The camera, like most, supports the RTSP protocol, enabling the transfer of image, sound and more (duplex).
I haven`t found any description of the specific addressing of this device on the Internet, but after scanning its available ports, the most interesting one is
554 turned out to be open - but none of the popular address combinations worked.
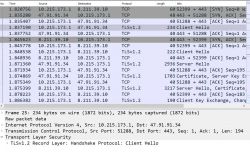
I decided to listen to her communication using PCAPdroid (on the phone), but the communication with the external cloud was immediately secured by TLS, so I didn`t learn much.
Frame examples:
Changing the connection mode to AP helped, I reset to the factory and connected directly.
It turned out that the application easily uses only RTSP for communication and without encryption.
I saved sample packets from the phone while I was working and analyzed them.
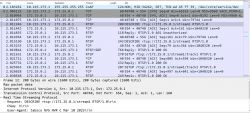
IMAGE STREAM
After initial analysis, I used a simple python script to capture the video stream.
Just use the ready-made openCV (it can natively decode this stream):
The above example takes image frames, scales to, and previews on screen.
Once prepared, we can use it freely, save it as a bitmap or paste a movie on the fly.
In my case, they go to rpi where AI analyzes the data and recordings (NVR) are created.
CONTROL OF CAMERA MECHANISMS
The camera has a rotating mechanism. I also discovered access to it in the RTSP transmission logs.
It turns out that the camera has the ability to read and respond to feedback messages. While working, I managed to call up a list of its parameters:
To manage these settings, you must send the appropriate frame with the command.
Surprisingly, the control commands run without logging in!
The rotation is in 2 stages, first start:
then stop rotation:
The -cmd parameter indicates the type of action (as listed above)
The time between sending packets is also dependent on the -data2 55 parameter (speed).
Another example, setting the date and time:
Below is an example class for handling rotation (up - down), which I wrote after understanding the command structure, and I am gradually adding new ones.
As I mentioned above, the camera can be rotated by controlling the rotation time and speed, and due to the lack of position information, you have to remember their number for each position change.
It certainly saves the last ones itself, because it sets them after a restart.
class="notranslate"> DISCONNECTING FROM THE MANUFACTURER`S CLOUD
Being able to freely control the camera, I left it connected to my LAN, but blocked its access to the Internet on the router. In this situation, the manufacturer`s application does not see the camera, it considers its status as offline and no data is sent.
However, this means that there is no access from the outside.
In my case it doesn`t matter, the camera is controlled by rpi, the image is sent to it, I have another way of viewing it - restream via my internal www.
Additionally, I have a public IP, my own openVPN server, and my devices (telephone, computer, etc.) are usually connected when I am outside, so they behave like in a LAN.
CONCLUSIONS
The camera generates quite a good image both during the day and at night, and additionally has LED illumination (white and IR).
I have virtually full access to it and the ability to control its parameters.
Currently, the image from it goes to rpi, where it is analyzed by AI. The camera observes the road in front of the house. Recognizes movement, its direction, moving objects (person, car), works on tracking and following the object, etc.
Probably most of these types of cheap IP cameras can be used without the original and UNSAFE manufacturer`s software, but then you need your own additional software.
Mr.
Below I will present a brief technical description of the device itself and steps to free it from the manufacturer`s cloud without changing the firmware.

I bought the camera on a well-known auction site, it cost PLN 75 then, now it costs PLN 85.

TECHNICAL DESCRIPTION
Technical data according to the seller:
Quote:
Waterproof: IP65 - the camera is resistant to rain, snow and other difficult weather conditions.
Connection type: WiFi - wireless connection of the camera to the home Internet network, providing easy access and remote control.
Recording resolution: 1080p (Full HD) - provides high-quality, detailed video image.
Zoom function: digital 4x
Antenna: 5dBi - provides a strong and stable WiFi signal, increasing the range and reliability of the wireless connection.
WiFi standard: 2.4GHz - compatible with most home routers, offering easy configuration and stable connection.
Camera program: Ease Life - an intuitive mobile application that allows you to easily manage your camera.
Power supply: DC 5V/2A
Infrared diodes: 21x IR LED - allow for clear viewing in complete darkness, also at night.
Recording function: microSD card / cloud - offers flexible options for saving recordings, both locally on a microSD card and remotely in the cloud.
Supported cards: microSD up to 128GB
Photo function: yes
To install the camera, use the appropriate application (Aview) available for mobile devices.
Using it, we can connect it to the home WiFi network (STA) or use it in AP mode (connect to its hotspot).
To be able to connect to the camera remotely, we need to log it into the Alibaba cloud (CN) and everything that happens to it goes through their servers (!).
This creates a huge danger because we have a foreign device in our LAN with full access to the network, and I don`t need to explain what can be done in such a configuration..
The device can be easily disassembled, 3 screws connect the balls to the camera and the whole thing is suspended on the ears of the rotating mechanism (1 screw).
I had to disassemble it to replace the power cable - the original one was a 15 cm cable with a plug, I replaced it with a longer one.
I don`t want to go into the details of the construction - one note, the rotation mechanisms do not have information about the position, everything is based on the number of rotation steps,
at startup, full-range calibration must occur in both axes.
Below are some photos of the interior.
Main board:

WiFi module:

Motor controls and their appearance:



LISTENING TO THE PROTOCOL
The camera, like most, supports the RTSP protocol, enabling the transfer of image, sound and more (duplex).
I haven`t found any description of the specific addressing of this device on the Internet, but after scanning its available ports, the most interesting one is
554 turned out to be open - but none of the popular address combinations worked.
I decided to listen to her communication using PCAPdroid (on the phone), but the communication with the external cloud was immediately secured by TLS, so I didn`t learn much.
Frame examples:

Changing the connection mode to AP helped, I reset to the factory and connected directly.
It turned out that the application easily uses only RTSP for communication and without encryption.
I saved sample packets from the phone while I was working and analyzed them.

IMAGE STREAM
After initial analysis, I used a simple python script to capture the video stream.
Just use the ready-made openCV (it can natively decode this stream):
Code: Python
The above example takes image frames, scales to, and previews on screen.
Once prepared, we can use it freely, save it as a bitmap or paste a movie on the fly.
In my case, they go to rpi where AI analyzes the data and recordings (NVR) are created.
CONTROL OF CAMERA MECHANISMS
The camera has a rotating mechanism. I also discovered access to it in the RTSP transmission logs.
It turns out that the camera has the ability to read and respond to feedback messages. While working, I managed to call up a list of its parameters:
Quote:
1 Up_Start
2 Down_Start
3 Left_Start
4 Right_Start
5 Right_Up_Start
6 Right_Down_Start
7 Left_Up_Start
8 Left_Down_Start
9 PT_Stop
10 Zoom_Tele - max zoom 12
11 Zoom_Wide - min zoom 1
12 Zoom_Stop
13 Focus_Near
14 Focus_Far
15 Focus_Stop
17 IRIS_CLOSE
18 IRIS_Stop
To manage these settings, you must send the appropriate frame with the command.
Surprisingly, the control commands run without logging in!
The rotation is in 2 stages, first start:
Code: Bash
then stop rotation:
Code: Bash
The -cmd parameter indicates the type of action (as listed above)
The time between sending packets is also dependent on the -data2 55 parameter (speed).
Another example, setting the date and time:
Code: Bash
Below is an example class for handling rotation (up - down), which I wrote after understanding the command structure, and I am gradually adding new ones.
Code: Python
As I mentioned above, the camera can be rotated by controlling the rotation time and speed, and due to the lack of position information, you have to remember their number for each position change.
It certainly saves the last ones itself, because it sets them after a restart.
class="notranslate"> DISCONNECTING FROM THE MANUFACTURER`S CLOUD
Being able to freely control the camera, I left it connected to my LAN, but blocked its access to the Internet on the router. In this situation, the manufacturer`s application does not see the camera, it considers its status as offline and no data is sent.
However, this means that there is no access from the outside.
In my case it doesn`t matter, the camera is controlled by rpi, the image is sent to it, I have another way of viewing it - restream via my internal www.
Additionally, I have a public IP, my own openVPN server, and my devices (telephone, computer, etc.) are usually connected when I am outside, so they behave like in a LAN.
CONCLUSIONS
The camera generates quite a good image both during the day and at night, and additionally has LED illumination (white and IR).
I have virtually full access to it and the ability to control its parameters.
Currently, the image from it goes to rpi, where it is analyzed by AI. The camera observes the road in front of the house. Recognizes movement, its direction, moving objects (person, car), works on tracking and following the object, etc.
Probably most of these types of cheap IP cameras can be used without the original and UNSAFE manufacturer`s software, but then you need your own additional software.
Mr.
Cool? Ranking DIY