Inspecting OBK logs with ncat - shortcut without the Web application
Sometimes I like a short look in the logs of an OpenBeken device without starting the web app and open the "logs" menu.
Or I like to save or filter the logs over a longer period.
This can be easily achieved by the connecting to port 9000 of the device.
I learned about this feature from a comment from @miegapele on git and would like to share it here.
On linux you would probably use nc/netcat. So, e.g. when working on the Driver for DS1820, I used:
On Windows (if you didn't install WSL) my preferred "swiss army knife" for tasks like this is a windows port of "busybox" (I get the binary from here).
So you can just start a "shell" there with "busybox sh" and simply use the same command as above .
.
And if there are times, when you miss md5sum, awk or sed - it's also there in this useful little binary.
The access to the network log is not a full replacement for the log on the hardware UART. But I really like it, especially when "waiting" for entries in the log.
Or I like to save or filter the logs over a longer period.
This can be easily achieved by the connecting to port 9000 of the device.
I learned about this feature from a comment from @miegapele on git and would like to share it here.
On linux you would probably use nc/netcat. So, e.g. when working on the Driver for DS1820, I used:
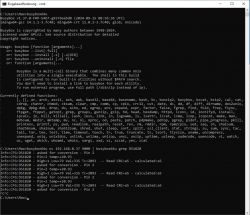
max@max-PC:~$ nc 192.168.0.37 9000 | grep DS1820
Info:CFG:DS1820 - asked for conversion - Pin 2
Info:CFG:DS1820 - Pin=2 temp=+19.37
Info:CFG:DS1820 - High=1 Low=54 Val=310 Tc=1937 -- Read CRC=79 - calculated:79
Info:CFG:DS1820 - asked for conversion - Pin 2
Info:CFG:DS1820 - Pin=2 temp=+19.37
Info:CFG:DS1820 - High=1 Low=54 Val=310 Tc=1937 -- Read CRC=79 - calculated:79
Info:CFG:DS1820 - asked for conversion - Pin 2
Info:CFG:DS1820 - Pin=2 temp=+19.37
Info:CFG:DS1820 - High=1 Low=54 Val=310 Tc=1937 -- Read CRC=79 - calculated:79
Info:CFG:DS1820 - asked for conversion - Pin 2
Info:CFG:DS1820 - Pin=2 temp=+19.37
Info:CFG:DS1820 - High=1 Low=54 Val=310 Tc=1937 -- Read CRC=79 - calculated:79
Info:CFG:DS1820 - asked for conversion - Pin 2
Info:CFG:DS1820 - Pin=2 temp=+19.37
Info:CFG:DS1820 - High=1 Low=54 Val=310 Tc=1937 -- Read CRC=79 - calculated:79
Info:CFG:DS1820 - asked for conversion - Pin 2
Info:CFG:DS1820 - Pin=2 temp=+19.37
Info:CFG:DS1820 - High=1 Low=54 Val=310 Tc=1937 -- Read CRC=79 - calculated:79
Info:CFG:DS1820 - asked for conversion - Pin 2
Info:CFG:DS1820 - Pin=2 temp=+19.37 On Windows (if you didn't install WSL) my preferred "swiss army knife" for tasks like this is a windows port of "busybox" (I get the binary from here).
So you can just start a "shell" there with "busybox sh" and simply use the same command as above

And if there are times, when you miss md5sum, awk or sed - it's also there in this useful little binary.
The access to the network log is not a full replacement for the log on the hardware UART. But I really like it, especially when "waiting" for entries in the log.



Comments
Very nice method, even I was not aware about that! Still, it could be also good to have logs stored in LittleFS, maybe? At least for debugging purposes and with some filtering, so we don't wear out flash... [Read more]
Cool! You could also do it with PowerShell # Prompt the user to enter the IP address $ip = Read-Host -Prompt "Enter the IP address to get logs from" $port = 9000 $client = New-Object System.Net.Sockets.TcpClient($ip,... [Read more]
I have CYGWIN in my Windows machine. Added nc and now it becomes very handy to filter log entries in real time. $ nc 192.168.1.250 9000 | awk '/SENSOR NOT/ {print}' Error:CMD:cmd... [Read more]
I've just tried this with PuTTy and works like a charm: https://obrazki.elektroda.pl/6384735500_1731864901_thumb.jpg https://obrazki.elektroda.pl/2622612300_1731864923_thumb.jpg [Read more]