Hi there!
I was given a pair of Konyks Priska FR, Smart Plug with integrated 16A energy meter (https://konyks.com/produit/priska-fr-dual-pack/).:

They work with Smart Life - so a Tuya based device.
So wanted to participate to the OpenBK adventure and being a massive adopter of Tasmota, enter the OpenBK adventure.
For the first plug, I cut the "female" part (top) - but this is not necessary. So don't do that !
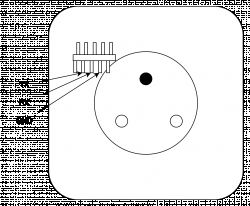
What you just need is to access the 3 pins GND/RX/TX of the CB2S (BK7231N) board.
This can be achieved by cutting a small plastic area - as per picture below:

Attaching a simple serial-TTL confirms the chip is well recognized, after keeping the button selected pushed twice, until the blue led blinks slowly.
Dumping the content of the flash - just in case:
And finally, flashing OpenBK:
Now, disconnect the device from power - wait ~ 10 seconds - and replug it. The OpenBK wifi SSID can be found
Here is the template:

I was given a pair of Konyks Priska FR, Smart Plug with integrated 16A energy meter (https://konyks.com/produit/priska-fr-dual-pack/).:

They work with Smart Life - so a Tuya based device.
So wanted to participate to the OpenBK adventure and being a massive adopter of Tasmota, enter the OpenBK adventure.
For the first plug, I cut the "female" part (top) - but this is not necessary. So don't do that !
What you just need is to access the 3 pins GND/RX/TX of the CB2S (BK7231N) board.
This can be achieved by cutting a small plastic area - as per picture below:

Attaching a simple serial-TTL confirms the chip is well recognized, after keeping the button selected pushed twice, until the blue led blinks slowly.

root@ubuntu:/work/bk7231tools# python3 -m bk7231tools chip_info -d /dev/ttyUSB0
BK72xx connected - protocol: FULL, chip: BK7231N, bootloader: BK7231N_1_0_1, chip ID: 0x7231c, boot version: None
Connected! Chip info: BK7231N / Flash ID: eb 60 15 / Flash size: 0x200000 / Protocol: FULL
Dumping the content of the flash - just in case:
root@ubuntu:/work/bk7231tools# python3 -m bk7231tools read_flash -d /dev/ttyUSB0 -s 0 dump2.bin
this may result in unpredictable behaviour
BK72xx connected - protocol: FULL, chip: BK7231N, bootloader: BK7231N_1_0_1, chip ID: 0x7231c, boot version: None
Connected! Chip info: BK7231N / Flash ID: eb 60 15 / Flash size: 0x200000 / Protocol: FULL
Reading 2097152 bytes from 0x0
Reading 4k page at 0x000000 (0.00%)
Reading 4k page at 0x001000 (0.20%)
...
Reading 4k page at 0x1FF000 (99.80%)
And finally, flashing OpenBK:
root@ubuntu:/work/bk7231tools# python3 -m bk7231tools write_flash -d /dev/ttyUSB0 -s 0 -B ../OpenBK7231N_QIO_1.18.37.bin
BK72xx connected - protocol: FULL, chip: BK7231N, bootloader: BK7231N_1_0_1, chip ID: 0x7231c, boot version: None
Connected! Chip info: BK7231N / Flash ID: eb 60 15 / Flash size: 0x200000 / Protocol: FULL
Writing 1220464 bytes to 0x0
Trying to unprotect flash memory...
Erasing and writing at 0x0 (0.00%)
- Checking block pre-erase @ 0x0
- Trying to erase block @ 0x0
- Checking block post-erase @ 0x0
- Erase succeeded @ 0x0
Erasing and writing at 0x1000 (0.34%)
Erasing and writing at 0x2000 (0.67%)
...
Erasing at 0x128000 (99.34%)
Erasing and writing at 0x129000 (99.68%)
OK!
Now, disconnect the device from power - wait ~ 10 seconds - and replug it. The OpenBK wifi SSID can be found
Here is the template:
{
"vendor": "Konyks",
"bDetailed": "0",
"name": "Konyks Priska FR",
"model": "Priska",
"chip": "BK7231N",
"board": "CB2S",
"flags": "1024",
"keywords": [
"konyks",
"priska"
],
"pins": {
"6": "BL0937CF;0",
"7": "BL0937CF1;0",
"8": "Rel;1",
"10": "WifiLED_n;0",
"11": "LED_n;1",
"24": "Btn;1",
"26": "BL0937SEL;0"
},
"command": "",
"image": "https://obrazki.elektroda.pl/8439438700_1739645788.jpg",
"wiki": "https://www.elektroda.com/rtvforum/viewtopic.php?p=21443038#21443038"
}








