We've been recently looking for a way to buy brand new Tuya modules, especially CB3S/CB2S (BK7231N) and WB2S (BK7231T). BK7231N is a bit newer and has more advanced support in OpenBeken (deep sleep and WS2812B), so it was our primary focus. Here I will write down our experience.
Our modules were ordered from a Chinese reseller, the unit price is about 2% per piece, we weren't sure whether they are reused or resold by Tuya, so we decided to make some tests.
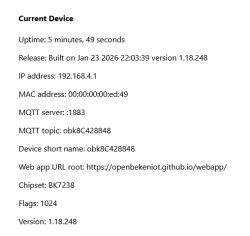
First module we'll test is WB2S:

It comes in a nice strip form:

We've checked the flash content with out flasher:
https://github.com/openshwprojects/BK7231GUIFlashTool
Suprisingly, something is there:
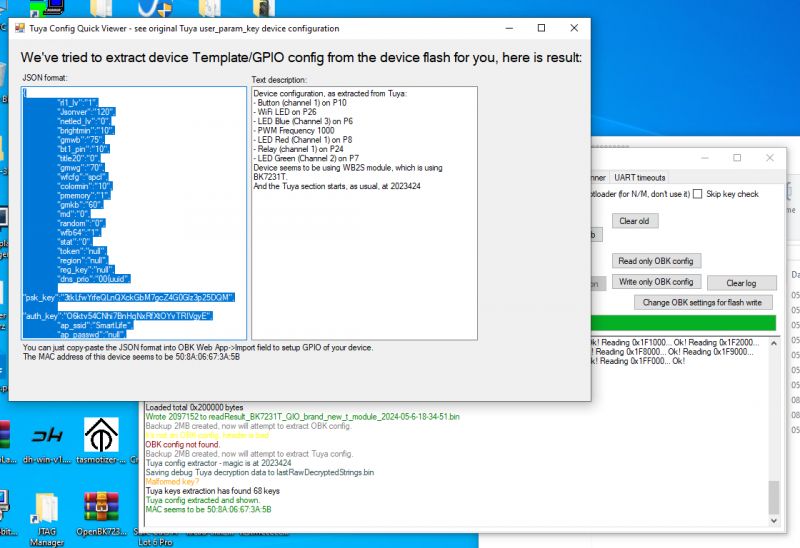
This device already contains a SmartLife flash dedicated for something that looks like a RGB lamp with extra Relay, Button and WiFi LED. It even has specified PWM frequency. It must have been dedicated to run in some smart device...
Then we also flashed OBK:
https://github.com/openshwprojects/OpenBK7231T_App
OBK access point shows up correctly:
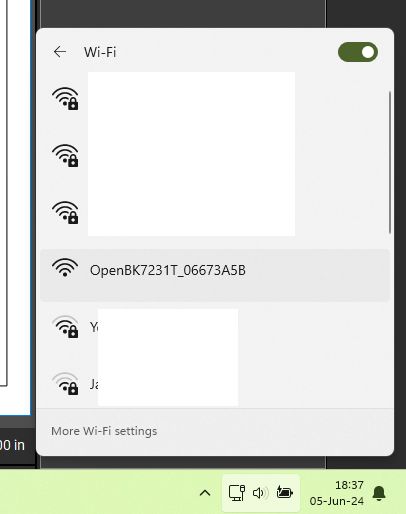
And it's possible to configure OBK easily:
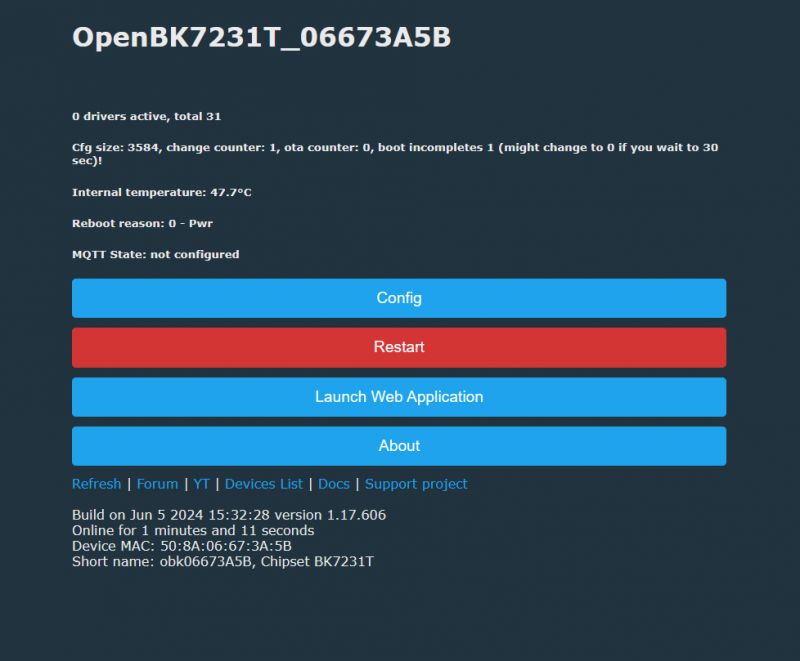
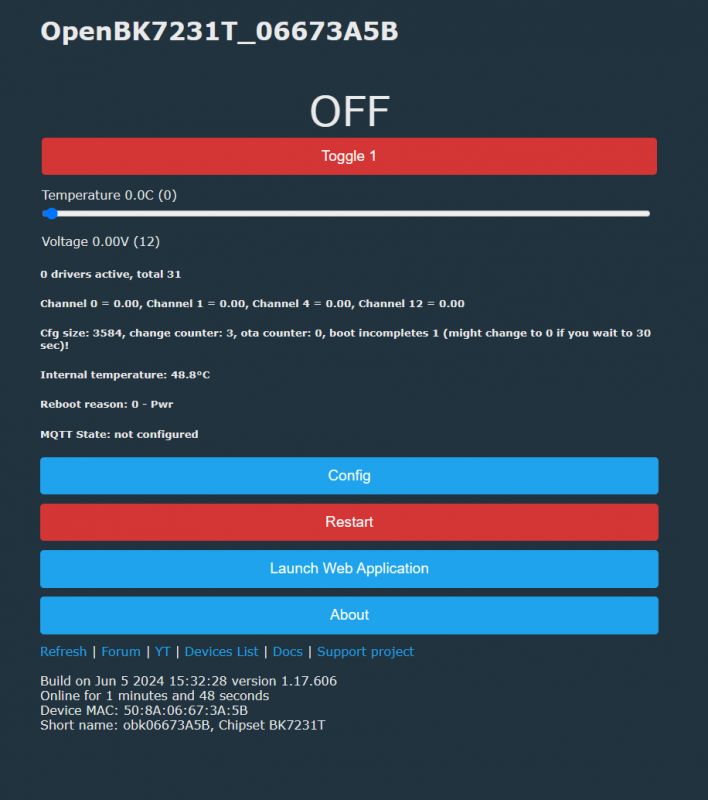
Second module we'll test is CB3S:
There is again something in the config:
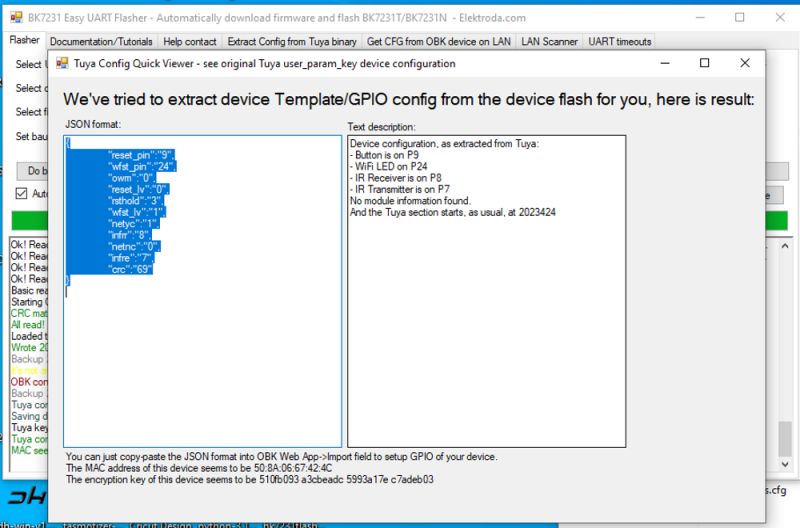
The config specifies a reset pin (button) on P9, a WiFi LED and both IR receiver and IR transmitter. It seems that this device was a smart IR remote module/repeater that could receive, learn and send IR signals.
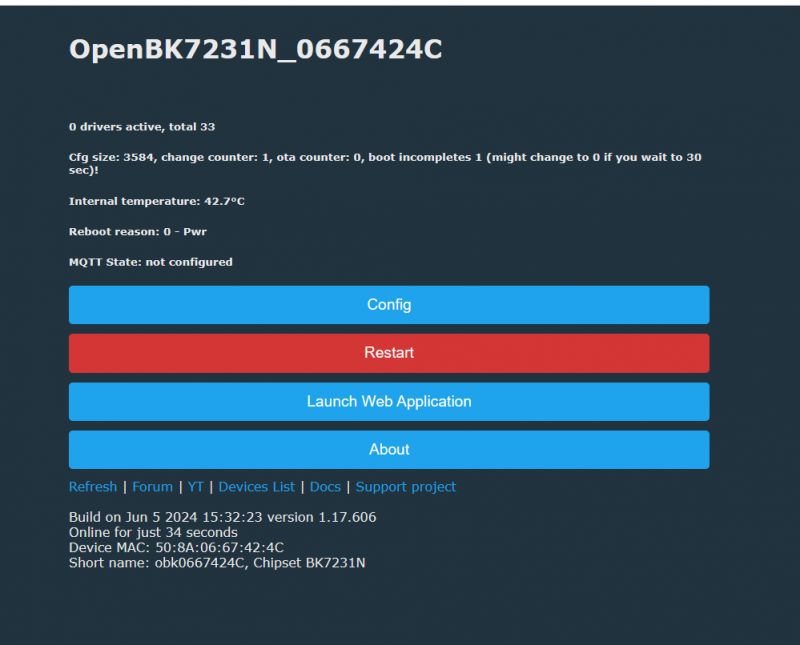
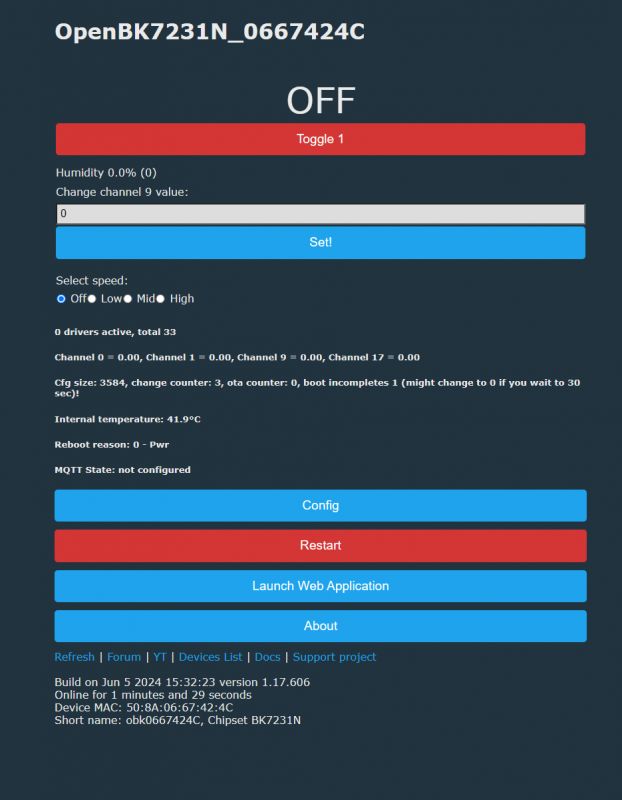
Again, we've tried to flash OBK on that - no problems:
Firmware dump:
https://github.com/openshwprojects/FlashDumps/commit/33924c257d8da78f0578341232158a95091f804d
Third module we'll test is CB2S:
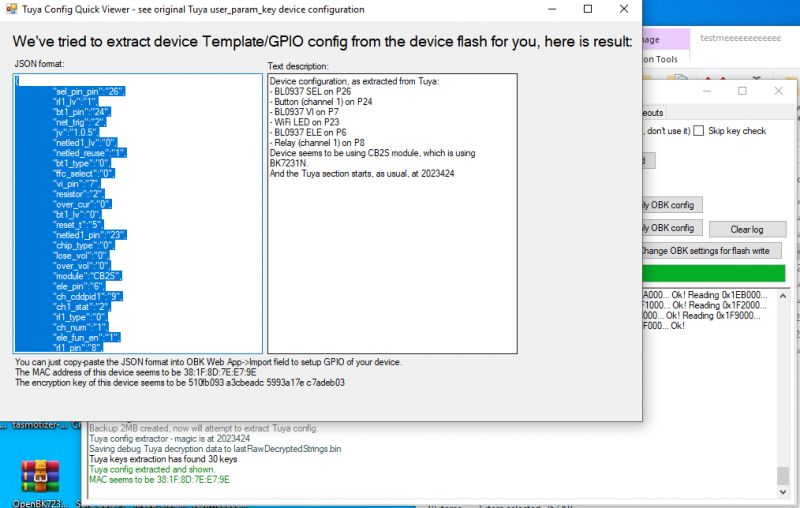
This time modulke seems to be coming from a BL0937 smart socket. BL0937 pins are clearly visible in the config. There is a also a Button, a Relay and WiFi LED.
Firmware dump:
https://github.com/openshwprojects/FlashDumps/commit/8e607e800c7e2a1b7b507ddfb7ab29f92aeba462
Conclusion: the bought Tuya modules seem to come from some Tuya production line. They already have flashed specific Tuya firmware for a given device type (like a RGB light, or a power metering plug, or an IR bridge) and are ready to be soldered inside it. They also contain already calibrated RF partition and work good with OpenBeken, so we haven't found any downsides to that. Hopefully they will be useful for us in our DIY projects.
Cool? Ranking DIY Helpful post? Buy me a coffee.