Winner Micro W803-E400 in RMW002 Smart Mini Switch: TW-803 Module, CozyLife Firmware & Boot Log

This device is another one of those 16A "DIY" mini switch/breakers that has been seen with quite a few different MCUs, modules and PCB layouts. Without high expectations it was ordered in the off-chance something new and interesting was inside. This time there was!











A Winner Micro W803-E400 chip on a TW-803 module. I've never received a production device with a W80x in. I have W800/W801 dev boards only - the Hi-Link HLK-W800-Kit, HLK-W801-Kit, HLK-W806-Kit and a HLK-B36 module.
It's the same CSKY/XuanTie XT804/CK804 architecture as the others. This family of chips is sometimes seen referred to as W80X.
At the moment we only have one W800 device in the device list (though it doesn't appear to have any pin assignments) - a WX300P RGB Strip Controller in the W800 flashing and development topic.
The TW-* module naming is reminiscent of the TW-02/03 labelling of the ThingsTurn W600 modules, but I've yet to find any official documentation to confirm a relation - only the ThingsTurn logo on this Taobao listing https://world.taobao.com/item/688026122927.htm

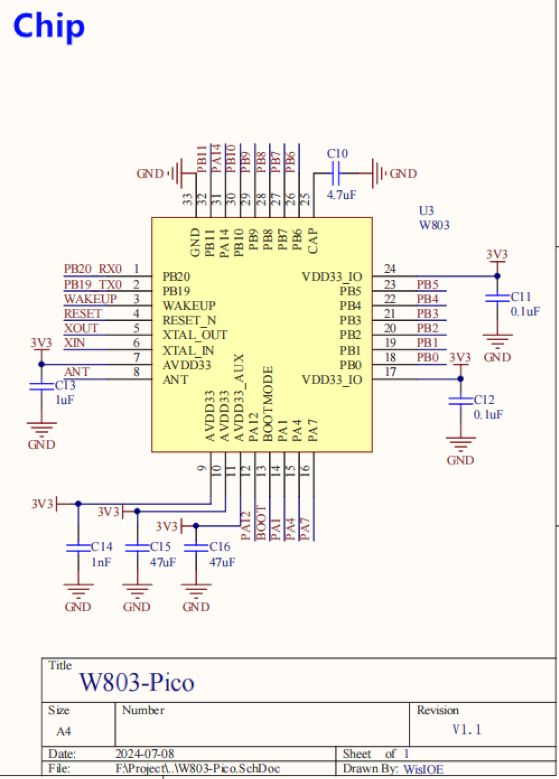
And it seems there is a W803Pico board https://doc.winnermicro.net/w800/en/latest/get_started/w803_pico.html from which chip pins can be seen
De-soldered module
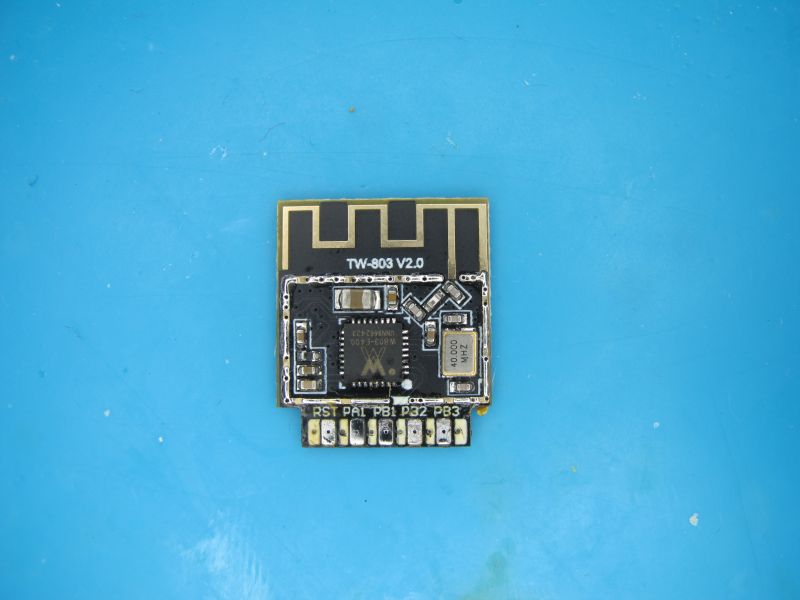

and from TX0 (PB19) we get the CozyLife boot log at 115200 baud
Code: Text
Before I flash OpenW800, erasing the factory firmware, I'd like to give my Python/W80x stub flash reader a go to see if I can take a backup. I've had no success getting a working device flashing these images back, but the read at least looks (mostly) sound.
The CK-Link method is an option too but only PA1 is routed out to a pad, PA4 would need to be a pogo pin or needle job.
Using python w800_flash_read_crc_flush_double.py (attached) and with RX0 (PA20) and TX0 (PA19) soldered up and connected to USB-TTL adaptor, I can read flash. Quick RST to ground for the script to catch and upload stub
Code: Text
2mb flash.
w800_flash_read.zip contains stub, script and my backup.
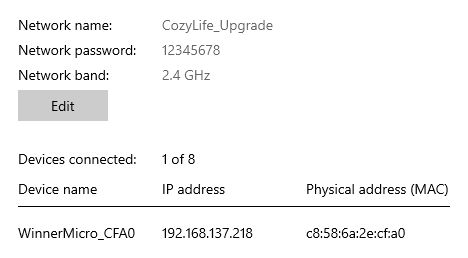
My initial finding in the backup is that it appears a factory SSID "CozyLife_Upgrade" is searched for and connected to with password "12345678". Interesting, maybe it'll then be open to OTA exploitation.
With that SSID available, it does indeed connect
on TX0 we see it listing SSIDs and stopping at CozyLife_Upgrade
Code: Text
Wireshark doesn't seem to suggest it tries to do anything on connection
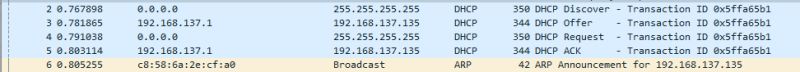
nmap
Code: Text
Similarly with "CozyLife_CC" broadcasting:
Code: Text
I do not see any AT commands in plain text in the fw backup.
There's probably more to investigate before the one-way trip to OpenW800
oh and Tuya still have these as downloads
https://airtake-public-data-1254153901.cos.ap...qcloud.com/smart/embed/pruduct/w803_0.0.1.zip
https://airtake-public-data-1254153901.cos.ap...qcloud.com/smart/embed/pruduct/w803_0.0.2.zip
UPDATE. Device was from Ali Express 20A option https://www.aliexpress.com/item/1005009631991603.html



Comments
With an STM32 running CK-Link Lite firmware and cabled as: https://obrazki.elektroda.pl/9844991400_1746439164_bigthumb.jpg PA4 pin connected using sewing needle held in place. https://obrazki.elektroda.pl/3034334300_1755725194_bigthumb.jpg... [Read more]