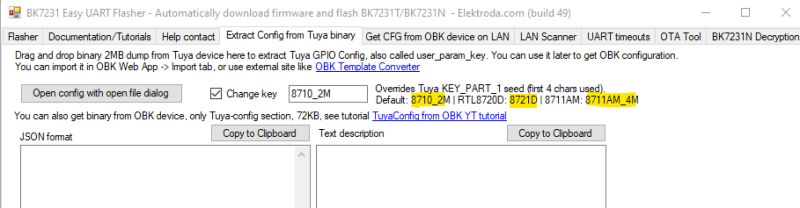
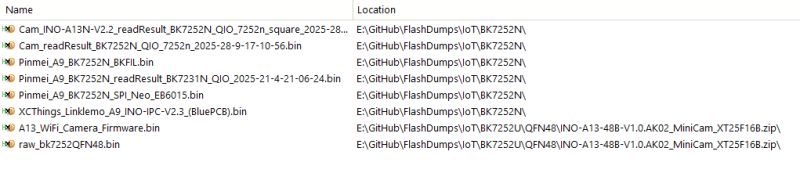
Additional info on how this camera works and how communications between the servers and the devices is done, can be found there: https://fusetim.me/posts/20251005-the-insecurity-camera/
The encryption of the packets is actually broken, and we could try to recover the camera traffic from there. Unfortunately, the AV packet description has already changed since the last available commit on the PPRPC/core project.
Added after 18 [minutes]:
>>21708767
The recently uploaded XCThings_Linklemo_A9_INO-IPC-V2.3_(BluePCB) firmware contains the exact same "secret" and is likely to use the exact same encryption scheme.
The encryption of the packets is actually broken, and we could try to recover the camera traffic from there. Unfortunately, the AV packet description has already changed since the last available commit on the PPRPC/core project.
Added after 18 [minutes]:
>>21708767
The recently uploaded XCThings_Linklemo_A9_INO-IPC-V2.3_(BluePCB) firmware contains the exact same "secret" and is likely to use the exact same encryption scheme.