The ubiquitous A9 Mini Wi-Fi Camera, in its seemingly many forms, is a compact, budget-friendly smart surveillance device, often seen for as low as $1USD as a Welcome Deal on sites like Ali Express. Positioned as a security camera, baby monitor, spycam, camcorder, it is often advertised by sellers as being 4K, having night-vision/infra-red, AI, motion detection. It can usually be said that one or more of these claims is false or at best, exaggerated. The device that is the subject of this post is listed with these "sellpoints" on Ali:
-Xiaomi Mini Camera4k Wireless Wifi Remote Camera4K Ultra Clear Image Quality:Capture every detail with 4K resolution, ensuring clear and vivid footage even in low light.
-WiFi/IP/AP Flexible Connection:Seamless connectivity with multiple modes: WiFi, IP, or AP, for uninterrupted monitoring.
-Intelligent Mobile Detection:High-precision motion sensors trigger alerts, reducing false alarms and enhancing security.
-Portable Design with Magnetic Base:Easily place the camera in any corner with its magnetic base, saving space and ensuring flexibility.
-Long Term Battery Life:Reliable performance with a large capacity battery, ensuring worry-free operation.
I am immediately sceptical about it being 4K and having anything to do with Xiaomi!
My device was sourced from Ali here https://www.aliexpress.com/item/1005008584918966.html
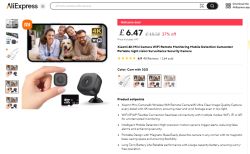
I'll now start by documenting the packaging and device before diving into the internals. Subsequent posts will detail the pairing/app user experience, as well as providing real images and videos created by the device.
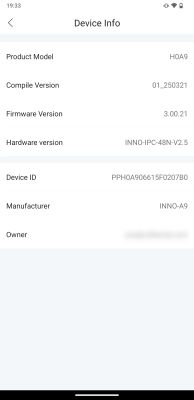
The box for this came marked with reference to "Shenzhen Pinmei Technology Co., Ltd".













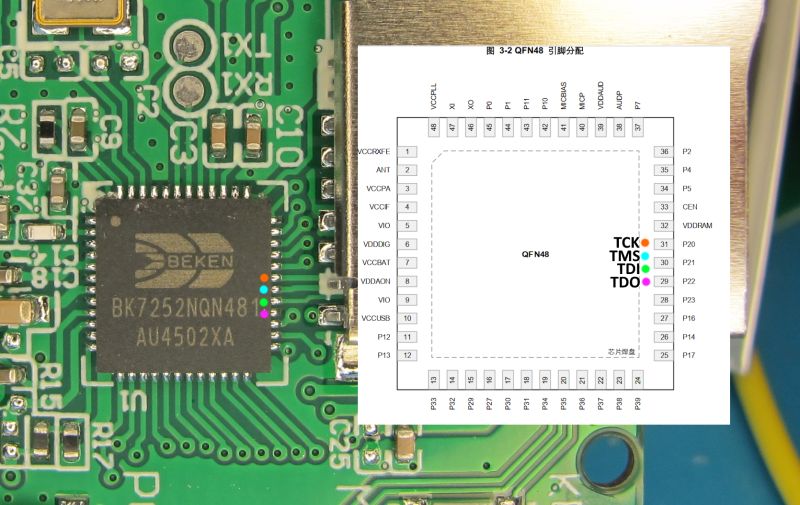
Inside we see a 2mb BK7252NQN481 - datasheet: https://www.elektroda.com/rtvforum/topic4118348.html#21526095









from TX1 @115200 baud
Code: Text
On one side are pads labelled TDI and TDO (accessible with camera ribbon removed). TMS and TCK are not so obvious.

TCK and TMS are these two:

I will later attempt SPI dump using these 4 pads as well as UART backup.
PCB text: INO-IPC-A9-V2.4 - I have not found FCC submissions for this device or company
From RX1/TX1 Easy Flasher reads in BK7252 mode but this skips bootloader. It also reads in N mode which covers the whole 2MB. Maybe BK7252N is more like BK7231N, it also seems to have a romcode like N. Maybe EF needs to have separate BK7252U and BK7252N modes. Maybe EF could have chip detect and it select the right mode if known? BK7252N CHIP_ID = 0x7252a
BKFIL is also happy with BK7252N where it wasn't interested in the older BK7252U.
Code: Text
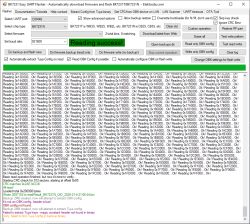
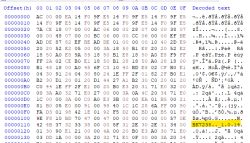
Flash ID is familiar EB6015 and coeff in efuse is 00e46d00 00e46d00 00e46d00 00e46d00
Code: Text
I propose a split of BK7252U and N folders in FlashDumps https://github.com/openshwprojects/FlashDumps/pull/28
If accepted my backups will land in https://github.com/openshwprojects/FlashDumps/tree/main/IoT/BK7252N
that's it for tonight with this cam
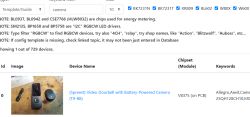
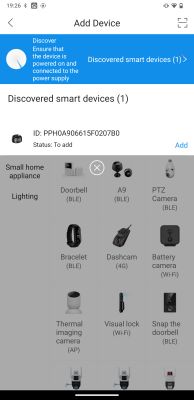
Sep 2025. Adding image for device list

Cool? Ranking DIY