Ah, I see. Nope. I haven't actually deployed that many smart devices for real use 😂. It's more about exploring and understanding electronics and everything OpenBeken of course

Czy wolisz polską wersję strony elektroda?
Nie, dziękuję Przekieruj mnie tam



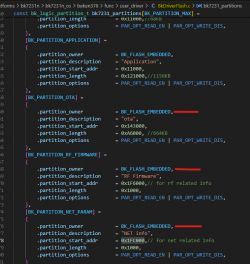
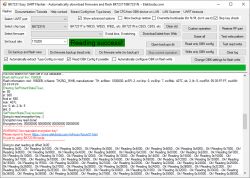

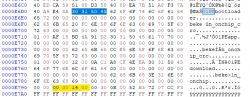

p.kaczmarek2 wrote:That's a great finding. What do you mean by standard bootloader? Do you mean that we need to.... recompile (?) or, should I say, encrypt the standard Tuya bootloader with the key you've given?
if [ "$BUILD_MODE" = "zerokeys" ]; then
echo "Using zero keys mode - for those non-Tuya devices"
./${ENCRYPT} ${APP_BIN_NAME}_${APP_VERSION}.bin 00000000 00000000 00000000 00000000 10000
#python mpytools.py bk7231n_bootloader_zero_keys.bin ${APP_BIN_NAME}_${APP_VERSION}_enc.bin
python mpytools.py bk7231n_bootloader_enc.bin ${APP_BIN_NAME}_${APP_VERSION}_enc.bin
else
echo "Using usual Tuya path"
./${ENCRYPT} ${APP_BIN_NAME}_${APP_VERSION}.bin 510fb093 a3cbeadc 5993a17e c7adeb03 10000
python mpytools.py bk7231n_bootloader_enc.bin ${APP_BIN_NAME}_${APP_VERSION}_enc.bin
fi
cp ${APP_BIN_NAME}_${APP_VERSION}.bin ${APP_BIN_NAME}_${APP_VERSION}_zeroKeys.bin
cp bk7231n_bootloader.bin bk7231n_bootloader_test.bin
if [ "$BUILD_MODE" = "zerokeys" ]; then
echo "Using zero keys mode - for those non-Tuya devices"
./${ENCRYPT} ${APP_BIN_NAME}_${APP_VERSION}.bin 00000000 00000000 00000000 00000000 10000
#python mpytools.py bk7231n_bootloader_zero_keys.bin ${APP_BIN_NAME}_${APP_VERSION}_enc.bin
python mpytools.py bk7231n_bootloader_enc.bin ${APP_BIN_NAME}_${APP_VERSION}_enc.bin
else
echo "Using usual Tuya path"
./${ENCRYPT} ${APP_BIN_NAME}_${APP_VERSION}.bin 510fb093 a3cbeadc 5993a17e c7adeb03 10000
./${ENCRYPT} bk7231n_bootloader_test.bin 510fb093 a3cbeadc 5993a17e c7adeb03 0
python mpytools.py bk7231n_bootloader_enc.bin ${APP_BIN_NAME}_${APP_VERSION}_enc.bin
fi
./${BEKEN_PACK} config.json
cp ${APP_BIN_NAME}_${APP_VERSION}.bin ${APP_BIN_NAME}_${APP_VERSION}_zeroKeys.bin
cp bk7231n_bootloader.bin bk7231n_bootloader_test.bin
cp bk7231n_bootloader.bin bk7231n_bootloader_dvd.bin
if [ "$BUILD_MODE" = "zerokeys" ]; then
echo "Using zero keys mode - for those non-Tuya devices"
./${ENCRYPT} ${APP_BIN_NAME}_${APP_VERSION}.bin 00000000 00000000 00000000 00000000 10000
#python mpytools.py bk7231n_bootloader_zero_keys.bin ${APP_BIN_NAME}_${APP_VERSION}_enc.bin
python mpytools.py bk7231n_bootloader_enc.bin ${APP_BIN_NAME}_${APP_VERSION}_enc.bin
else
echo "Using usual Tuya path"
./${ENCRYPT} ${APP_BIN_NAME}_${APP_VERSION}.bin 510fb093 a3cbeadc 5993a17e c7adeb03 10000
./${ENCRYPT} bk7231n_bootloader_test.bin 510fb093 a3cbeadc 5993a17e c7adeb03 0
./${ENCRYPT} bk7231n_bootloader_dvd.bin 4862379A 8612784B 85C5E258 75754528 0
python mpytools.py bk7231n_bootloader_enc.bin ${APP_BIN_NAME}_${APP_VERSION}_enc.bin
fi
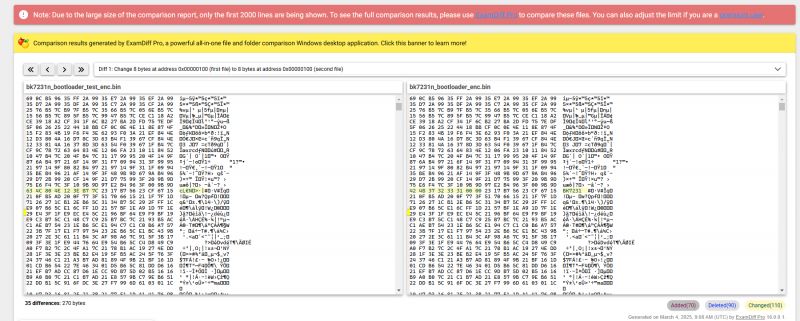
./${ENCRYPT} bk7231n_bootloader_test.bin 510fb093 a3cbeadc 5993a17e c7adeb03 0
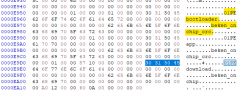
00000100+8
-> 42 4B 37 32 33 31 00 00 BK7231..
-> 63 4C 80 4E 12 3E B7 7C cL.N.>.|
0000E95C+212
-> 30 31 50 45 62 6F 6F 74 6C 6F 61 64 65 72 00 00 00 00 00 00 00 00 00 00 00 00 00 00 62 65 6B 65 6E 5F 6F 6E 63 68 69 70 5F 63 72 63 00 00 00 00 00 00 00 00 00 00 00 00 00 00 01 00 00 00 00 00 30 31 50 45 61 70 70 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 62 65 6B 65 6E 5F 6F 6E 63 68 69 70 5F 63 72 63 00 00 00 00 00 00 00 00 00 00 01 00 00 87 10 00 00 00 00 00 30 31 50 45 64 6F 77 6E 6C 6F 61 64 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 62 65 6B 65 6E 5F 6F 6E 63 68 69 70 00 00 00 00 00 00 00 00 00 00 00 00 00 A0 12 00 00 60 0A 00 00 00 00 00 -- -- -- -- -- -- -- -- -- -- -- -- -- -- -- -- -- -- -- -- 01PEbootloader..............beken_onchip_crc....................01PEapp.....................beken_onchip_crc....................01PEdownload................beken_onchip.................`..........................
-> B1 2E 3F 98 E3 08 00 A9 ED 00 0E B9 E4 05 6F DD 81 7F 6F DD 81 47 6F DD 81 4F 6F DD E3 32 04 B8 EF 00 00 B3 E2 CF 07 AD DE CC 1C BE 81 B7 6E DD 81 BF 6E DD 81 87 6E DD 81 8F 6F DD 81 97 6E DD B1 AE 3E 98 E0 97 1E DD 81 EF 6E DD 81 F7 6E DD 81 FF 6E DD 81 C7 6E DD 81 CF 6E DD E3 B2 05 B8 EF 80 01 B3 E2 4F 07 AD DE 4C 1C BE 81 37 6E DD 81 3F 6E DD 81 07 6F DD 81 88 7E DD 81 17 6E DD B1 2E 3E 98 E5 08 19 B3 ED 00 0F B9 81 77 6E DD 81 7F 6E DD 81 47 6E DD 81 4F 6E DD E3 32 05 B8 EF 00 01 B3 E2 CF 00 AD 81 AF 69 DD 81 B7 69 DD 81 BF 69 DD 81 27 7B DD 81 EF 63 DD 81 97 69 DD 7E 60 96 22 FF FF FF FF FF FF FF FF FF FF FF FF FF FF FF FF ..?...........o...o..Go..Oo..2................n...n...n...o...n...>.......n...n...n...n...n..........O...L...7n..?n...o...~...n...>..........wn...n..Gn..On..2............i...i...i..'{...c...i.~`."................
./${ENCRYPT} bk7231n_bootloader_test.bin 510fb093 a3cbeadc 5993a17e c7adeb03 0 -crc
divadiow wrote:
Interesting, I've changed ALL keys in the build.sh into the Uascent one, so N and M QIO should both boot, neither do.
https://github.com/openshwprojects/OpenBK7231...mits/d2c2eda407d011406ef3158e0c91244e79383871
echo "Will do extra step - for zero keys/dogness"
cp ${APP_BIN_NAME}_${APP_VERSION}_zeroKeys.bin ${APP_BIN_NAME}_${APP_VERSION}.bin
echo "Will do zero keys encrypt"
./${ENCRYPT} ${APP_BIN_NAME}_${APP_VERSION}.bin 00000000 00000000 00000000 00000000 10000
echo "Will do zero mpytools.py"
python mpytools.py bk7231n_bootloader_enc.bin ${APP_BIN_NAME}_${APP_VERSION}_enc.bin
echo "Will do zero BEKEN_PACK"
./${BEKEN_PACK} config.json
echo "Will do zero qio"
cp all_1.00.bin ${APP_BIN_NAME}_QIO_${APP_VERSION}.bin
cp ${APP_BIN_NAME}_QIO_${APP_VERSION}.bin ../../${APP_PATH}/$APP_BIN_NAME/output/$APP_VERSION/OpenBK7231M_QIO_${APP_VERSION}.bin
cp ${APP_BIN_NAME}_UA_${APP_VERSION}.bin ../../${APP_PATH}/$APP_BIN_NAME/output/$APP_VERSION/OpenBK7231M_UA_${APP_VERSION}.bin
p.kaczmarek2 wrote:I'll see how far we can get
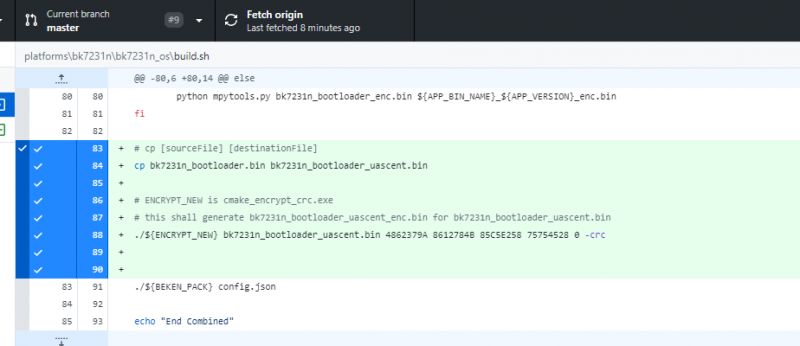
#
# UASCENT steps (4862379A 8612784B 85C5E258 75754528)
#
# Copy blank bootloader just to have it with "uascent" in name
# cp [sourceFile] [destinationFile]
cp bk7231n_bootloader.bin bk7231n_bootloader_uascent.bin
# Call encrypt like Divadiow did
# ENCRYPT_NEW is cmake_encrypt_crc.exe
# this shall generate bk7231n_bootloader_uascent_enc.bin for bk7231n_bootloader_uascent.bin
./${ENCRYPT_NEW} -enc bk7231n_bootloader_uascent.bin 4862379A 8612784B 85C5E258 75754528 -crc
# Copy blank-start App with zero keys bin
# cp [sourceFile] [destinationFile]
cp ${APP_BIN_NAME}_${APP_VERSION}_zeroKeys.bin ${APP_BIN_NAME}_${APP_VERSION}.bin
# Apply keys to the App
echo "Will do UASCENT encrypt"
# This will generate ${APP_BIN_NAME}_${APP_VERSION}_enc.bin
./${ENCRYPT} ${APP_BIN_NAME}_${APP_VERSION}.bin 4862379A 8612784B 85C5E258 75754528 10000
# Use mpytools.py to generate config.json for encrypted bootloader and encrypted app
echo "Will do UASCENT mpytools.py to generate config.json"
# python mpytools.py [BootloaderFile] [AppFile]
python mpytools.py bk7231n_bootloader_uascent_enc.bin ${APP_BIN_NAME}_${APP_VERSION}_enc.bin
# Use Beken Pack on created config.json to combine bootloader and app together into all_1.00.bin
echo "Will do UASCENT BEKEN_PACK"
./${BEKEN_PACK} config.json
echo "Will do UASCENT qio"
cp all_1.00.bin ${APP_BIN_NAME}_QIO_${APP_VERSION}.bin
cp ${APP_BIN_NAME}_QIO_${APP_VERSION}.bin ../../${APP_PATH}/$APP_BIN_NAME/output/$APP_VERSION/OpenBK7231N_UASCENT_QIO_${APP_VERSION}.bin
cp ${APP_BIN_NAME}_UA_${APP_VERSION}.bin ../../${APP_PATH}/$APP_BIN_NAME/output/$APP_VERSION/OpenBK7231N_UASCENT_UA_${APP_VERSION}.bin




