To be sure - does it run on single uascent device, or on multiple pieces?
Is OTA working? I guess not, as you mentioned earlier/?
Helpful post? Buy me a coffee.
Is OTA working? I guess not, as you mentioned earlier/?
Czy wolisz polską wersję strony elektroda?
Nie, dziękuję Przekieruj mnie tam



p.kaczmarek2 wrote:To be sure - does it run on single uascent device, or on multiple pieces?
p.kaczmarek2 wrote:OTA working? I guess not, as you mentioned earlier
insmod wrote:Actually, does unencrypted 1.0.1 bootloader contains partitions?
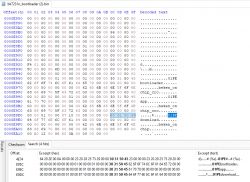
OpenBK7231N\platforms\bk7231n\bk7231n_os\tools\generate\package_tool\windows>cmake_encrypt_crc.exe
/**< @author Bekencorp */
/**< @version v5.0.0.7 */
ERROR: Invalid number of arguments
Usage: encrypt_crc tool <command> <options-argument pairs>
cmd -options usage and description/values
------------------------------------------------------------------------
encrypt_crc
-enc
infile.bin iutput bin file
passcode0 input passcode0
passcode1 input passcode0
passcode2 input passcode0
passcode3 input passcode0
-crc
-start-add
start_address default value = 0
-un-skip To un-skip keywords in chips ,such as addr = 0x100,default value = 0
--version | -v | version To print the current version of this utility
--help | -h | help To print this help message
echo "Using usual Tuya path"
./${ENCRYPT} ${APP_BIN_NAME}_${APP_VERSION}.bin 510fb093 a3cbeadc 5993a17e c7adeb03 10000
python mpytools.py bk7231n_bootloader_enc.bin ${APP_BIN_NAME}_${APP_VERSION}_enc.bin
(...)
echo "generate ota file"
./${RT_OTA_PACK_TOOL} -f ${APP_BIN_NAME}_${APP_VERSION}.bin -v $CURRENT_TIME -o ${APP_BIN_NAME}_${APP_VERSION}.rbl -p app -c gzip -s aes -k 0123456789ABCDEF0123456789ABCDEF -i 0123456789ABCDEF
./${TY_PACKAGE} ${APP_BIN_NAME}_${APP_VERSION}.rbl ${APP_BIN_NAME}_UG_${APP_VERSION}.bin $APP_VERSION
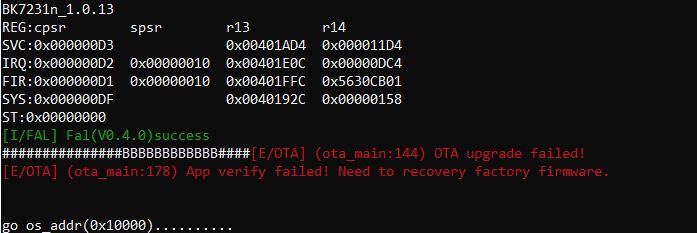
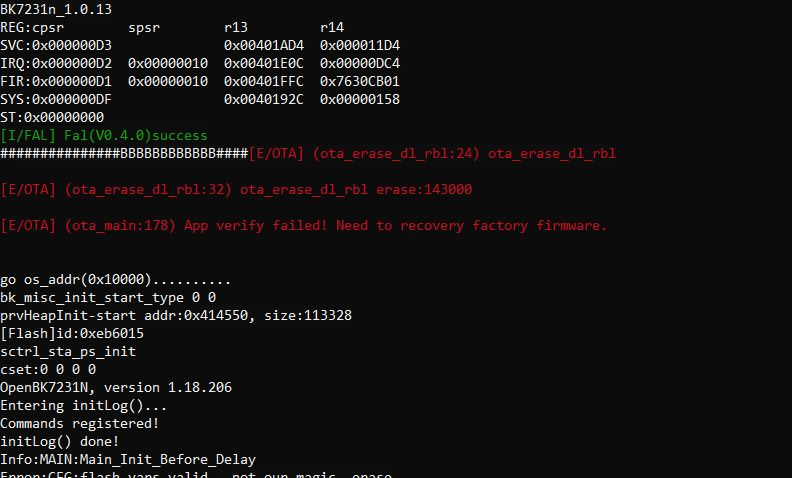
p.kaczmarek2 wrote:Why does even OTA fail? Do they use the keys to check OTA file?
p.kaczmarek2 wrote:Maybe we need -un-skip?
p.kaczmarek2 wrote:Would that mean OTA is also encrypted with those keys? I remember reading that it's not encrypted, so now I'm confused.
p.kaczmarek2 wrote:Nice, so we would need 3 binaries in relases? Zero keys (M), Uascent and classic N?
insmod wrote:What exactly is the problem with OTA?
insmod wrote:Does OTA work on BK7231M?
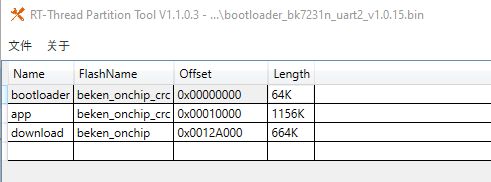
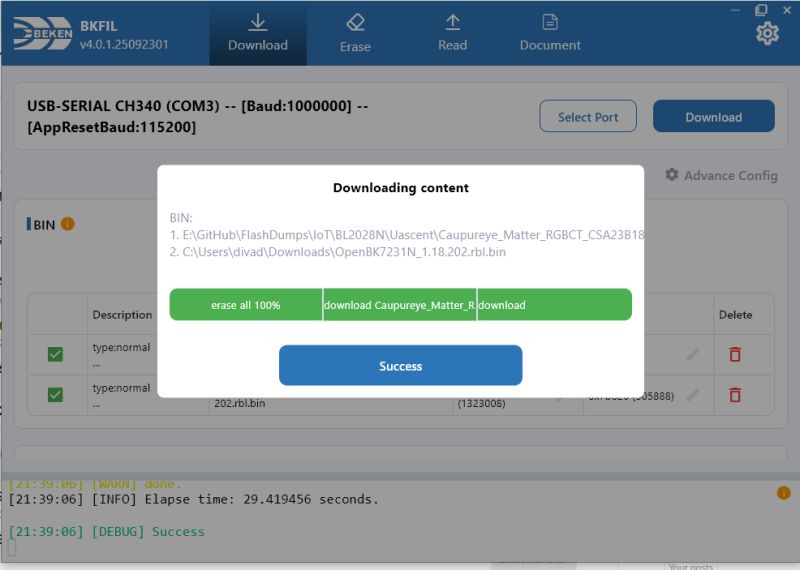
divadiow wrote:Ok cool. We'll feed that into the build for the uascent section and can finally, hopefully, release Uascent QIO in the BK7231N zip?
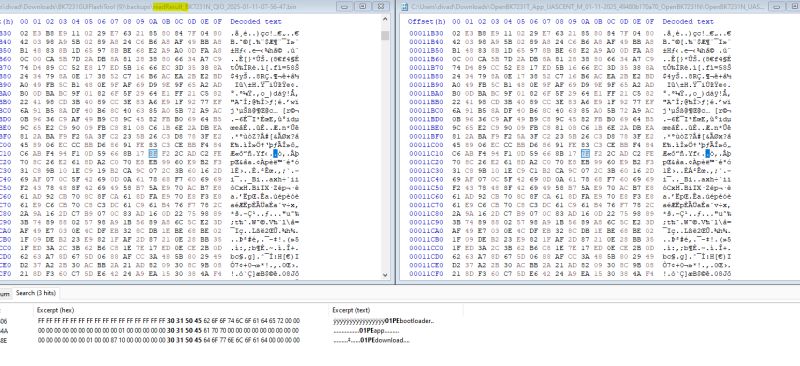

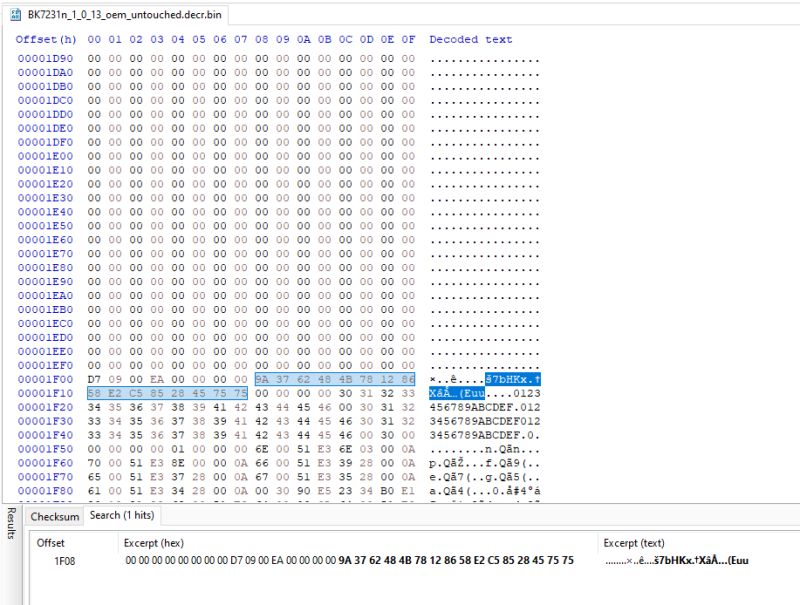
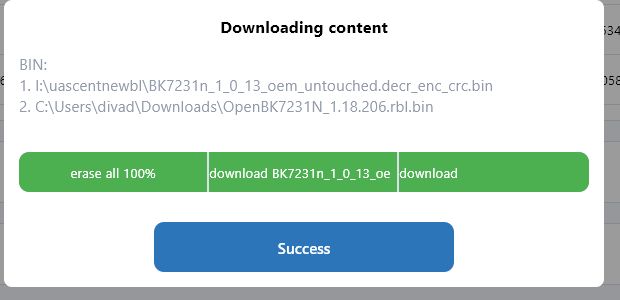
divadiow wrote:this is interesting https://github.com/mildsunrise/bk7231_key_calculator
| FileName | SBDV | Coeff | Coeff LE | ota.key | ota.iv | readResult_BK7231N_QIO_bulb_sber_e14_cblc9_2024-10-3-17-50-08.bin | SBDV-00117 | 7d1ff9b3e3ffefde5d93b57eefefeb8b | B3 F9 1F 7D DE EF FF E3 7E B5 93 5D 8B EB EF EF | 908f771bac2ff1aa619b897c14c5a88b | 1e647fab598d727c | readResult_BK7231N_QIO_sbdv_00050.bin | SBDV-00050 | d34fbdd3efcbeadefd97bbffc7bfff3b | D3 BD 4F D3 DE EA CB EF FF BB 97 FD 3B FF BF C7 | b4f9937b63a7c365f27bf8d06fb67978 | 53de9074383e2223 | OpenBK7231N_QIO_Sber_Fck.bin (contains LibreTiny) | SBDV-00115 | 79bffed7a3fbeafd5dd3abffdfbfff5b | D7 FE BF 79 FD EA FB A3 FF AB D3 5D 5B FF BF DF | BDB4CE110F4787C2F539BF50E30A14E0 | 46DE464946314329 | readResult_BK7231M_QIO_sbdv-00115_2025-29-8-16-28-19.bin | SBDV-00115 | 79bffed7a3fbeafd5dd3abffdfbfff5b | D7 FE BF 79 FD EA FB A3 FF AB D3 5D 5B FF BF DF | BDB4CE110F4787C2F539BF50E30A14E0 | 46DE464946314329 | readResult_BK7231N_QIO_SBDV-00027_2025-24-4-10-45-49.bin | SBDV-00027 | TUYA | readResult_BK7231N_QIO_bulb_sber2_2024-18-3-14-40-51.bin | SBDV-00117 | 7d1ff9b3e3ffefde5d93b57eefefeb8b | B3 F9 1F 7D DE EF FF E3 7E B5 93 5D 8B EB EF EF | 908f771bac2ff1aa619b897c14c5a88b | 1e647fab598d727c | sber_lamp_BK7231N_1.0.8_stock_dump.bin | SBDV-00019 | 7fefb6fbabdbfbddffffaf7fc7edef17 | FB B6 EF 7F DD FB DB AB 7F AF FF FF 17 EF ED C7 | CE11F17490393890CD149E0F25FBE10D | E5F12CB853A63E30 | readResult_BK7231N_QIO_2024-17-3-11-58-59_sber_e14-2.bin | SBDV-00117 | 7d1ff9b3e3ffefde5d93b57eefefeb8b | B3 F9 1F 7D DE EF FF E3 7E B5 93 5D 8B EB EF EF | 908f771bac2ff1aa619b897c14c5a88b | 1e647fab598d727c | readResult_BK7231N_QIO_2343_2024-28-1-10-44-05_sber_e14.bin | SBDV-00117 | 7d1ff9b3e3ffefde5d93b57eefefeb8b | B3 F9 1F 7D DE EF FF E3 7E B5 93 5D 8B EB EF EF | 908f771bac2ff1aa619b897c14c5a88b | 1e647fab598d727c | OpenBK7231M_QIO_SBER_DEL.bin | SBDV-00123 | d74ff1d7a3dbefdc5fdfa77fdfafffd3 | D7 F1 4F D7 DC EF DB A3 7F A7 DF 5F D3 FF AF DF | 5AC0EE0B2379005E3F52CCA49B2D741D | 8BCC2EF2EDEC53C7 |




