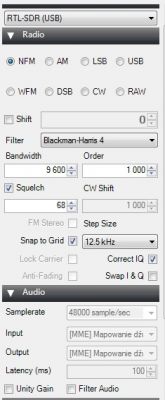
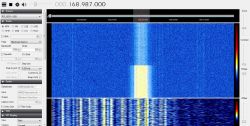
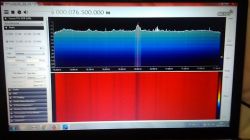
Police MOTOTRBO cannot be decoded with DSD, because DSD cannot break a binary key, only once. And two, DSD doesn't even have the option of typing the key. If you are familiar with Linux, you can do it with Airprobe. The same goes for TETRA. Airprobe is a GSM demodulator, but apparently it can handle both TETRA and MOTOTRBO. The process of "getting" the keys - because there are two in TETRA, it is the same as in the case of WPA2, that is, catching packets and then Kraken ... GSM dump can also be useful. You will need a powerful graphics card that supports CUDA or, in the case of Radeonstream, to search the packets. Preferably several cards with, say, 300 cores. You can do one too, but you have to be "a little" patient. The matter is greatly complicated by the lack of rainbow tables. They are standard SSSids for WPA2. You have to generate custom ones yourself. There are for GSM, but ... they are 2TB files. Neither MOTOTRBO nor TETRA is available, and I do not know what such boards should look like and whether there would be any sense in generating and sharing. It makes no sense as such arrays are generated for one specific network and it is not possible to create a universal one. Therefore, in the case of GSM, it is as much as 2 TB because someone went to so much trouble to generate networks for most of the networks. Probably the Germans did it on some university machine for big calculations. TETRA has two dynamic keys - that is, two variables and assigned based on a fixed algorithm. In GSM it is identical and the GSM dump catches packets nicely and the Kraken later searches for login keys that we sign to Airprobe. This means that we grab millions of packets first, and then act on them. Fortunately, GSM and derivatives emit hundreds of thousands of keys in one hour, or maybe more. One BTS can handle 50 users at a time. Within an hour, it will be different users .... In the case of MOTOTRBO there is one, static key. Something similar to the old WEP that kids in kindergartens today break using "press and wait a few minutes" programs. I am surprised by such nonchalance in the service, but after all, it seems to be quite a handicap for the listeners. Unsecured transmission is provided by e.g. an ambulance service in the vicinity of 168MHz. Major services use TETRA. Until recently, this system was extremely difficult to eavesdrop on, just like GSM. Today ... any radio broadcast can be intercepted and decoded. It's just a matter of computer processing power. But with the right set of graphics cards, you can do a lot in a reasonable amount of time. As you can see odbiordaski you already have, now some computer with equipment for about 6-7 thousand, Linux support from your finger, several drives for several TB of files and we go  I warn you right away, it is not in line with Polish law. Analog broadcasting police can be listened to, but breaking the security of intentionally encoded transmission is against the law. With GSM, unsecured network information can be received. These are SMS-CB with announcements and various discussions, also BTS names, BTS often send network information in the form of a network name but also with a street name. You can read this without risking the later choice between secretary and sucker. Of course, data reception and data breaking is difficult to detect, because it is passive hacking - nobody sends packets over the network. Because there is no such need, the network itself generates millions of packets. It does not change the fact that I will repeat that breaking the transmission security is punishable by law. The video describes the LEGAL GSM reception process. Mrs. Shannon (Yes! Married!) Describes exactly, runs like a child's hand, what exactly needs to be installed and how. Not to mention the "pluings". Good knowledge of the English language required. I wish you successes!
I warn you right away, it is not in line with Polish law. Analog broadcasting police can be listened to, but breaking the security of intentionally encoded transmission is against the law. With GSM, unsecured network information can be received. These are SMS-CB with announcements and various discussions, also BTS names, BTS often send network information in the form of a network name but also with a street name. You can read this without risking the later choice between secretary and sucker. Of course, data reception and data breaking is difficult to detect, because it is passive hacking - nobody sends packets over the network. Because there is no such need, the network itself generates millions of packets. It does not change the fact that I will repeat that breaking the transmission security is punishable by law. The video describes the LEGAL GSM reception process. Mrs. Shannon (Yes! Married!) Describes exactly, runs like a child's hand, what exactly needs to be installed and how. Not to mention the "pluings". Good knowledge of the English language required. I wish you successes!
https://www.youtube.com/watch?v=FqtJ-TvtLTQ
https://www.youtube.com/watch?v=FqtJ-TvtLTQ