Hi , I have a question for you.
Well, I have a Matter 4CH device , I wanted to upload OBK, but of course it is not so simple.
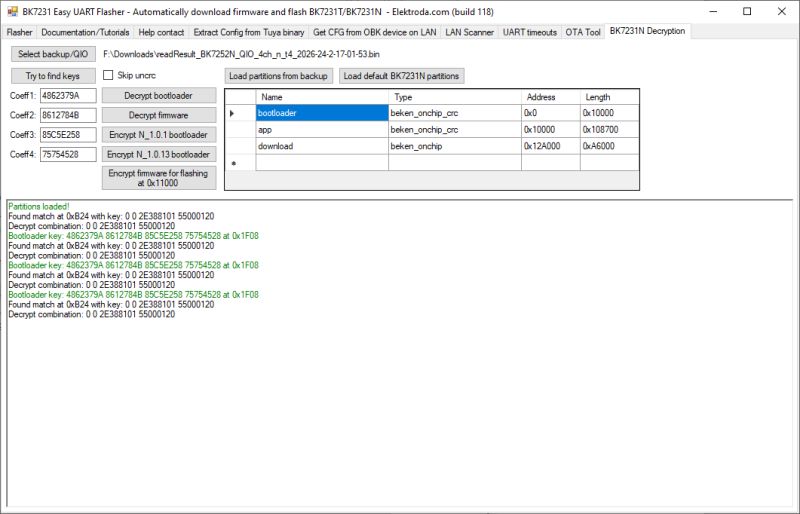
The device is based on a BL2028 , and I have really uploaded the software many times , of course I have the ORI dump of the batch.
But Uploading any version from the current REALSE 1.18.264 , the module does not issue an AP , RF restore does not work , Entering WIFI and password does not work.
REALSE with the UA end does not work either, as I infer that this is the version intended for the UASENT device.
Tried in options upload BK7231N (T2,T34) with skip keys, BK7231M, and BK7231N (T4), of course bootloader remains orginals from Matter device.
The option that helped and the only one that works is to upload the file from this thread ENCRYPT_NEW_DOESBOOT_NOOTA_OpenBK7231N_UASCENT_QIO_bk7231m_qio_09b8b111cb80.bin
But, of course, the OTA does not work here, but the module starts, you can set everything to your liking, and this is the only version I was able to upload correctly to UAM028.
Can you, as experienced programmers, answer me why no other software will boot on this module?
Of course, the electronics is not a problem for me, but the programming and reverse engineering is a bit of a problem.
If someone needs the original batch of course I have it, and I can upload it here for review.
And maybe one more thing, I have a PIN (GPIO) list for this device, maybe you can tell me how to put it into the device directory, because I saw that it does not exist, and I have it.
Please help me to explain why only this one software works , others do not work with it ?