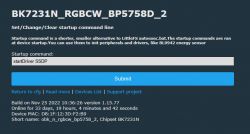
Yes it is planned, what exactly format of data do you need, the JSON? Which fields of JSON are you actively using? If just a few, I can add it for you relatively quick, but I need a detailed specs of what you need.
Helpful post? Buy me a coffee.

Czy wolisz polską wersję strony elektroda?
Nie, dziękuję Przekieruj mnie tam

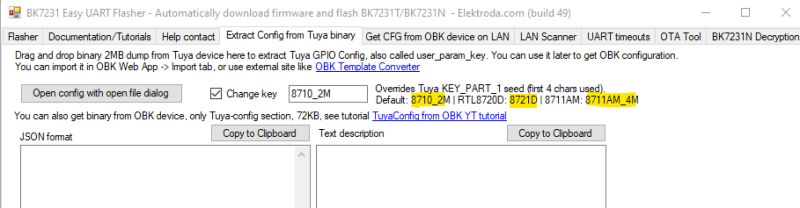
 Good afternoon friends
Good afternoon friends
kajarit wrote:But I couldn't find any info on these commands:
- startDriver
- linkTuyaMCUOutputToChannel
- setChannelType
backlog startDriver tuyaMCU; startDriver tmSensor; setChannelType 1 ReadOnly; linkTuyaMCUOutputToChannel 1 2 1; setChannelType 2 ReadOnly; linkTuyaMCUOutputToChannel 2 2 2; setChannelType 3 ReadOnly; linkTuyaMCUOutputToChannel 3 2 3; setChannelType 4 ReadOnly; linkTuyaMCUOutputToChannel 4 2 4; setChannelType 5 ReadOnly; linkTuyaMCUOutputToChannel 5 2 5;p.kaczmarek2 wrote:Hello @f616 , can you provide more technical information about both WiFi networks, or at least about the problematic one? Does it broadcast SSID ,what kind of encryption is used, etc?
Sun Dec 4 13:34:12 2022 daemon.info hostapd[2220]: ath0: STA fc:ec:da:8d:29:70 DRIVER: Send AUTH addr=c8:47:8c:01:23:45 status_code=0
Sun Dec 4 13:34:12 2022 kern.warn kernel: [2431717.610399] ath0: [c8:47:8c:01:23:45] recv auth frame with algorithm 0 seq 1
Sun Dec 4 13:34:12 2022 daemon.info hostapd[2220]: ath0: STA c8:47:8c:01:23:45 IEEE 802.11: associated
Sun Dec 4 13:34:12 2022 daemon.info hostapd[2220]: ath0: STA c8:47:8c:01:23:45 WPA: sending 1/4 msg of 4-Way Handshake
Sun Dec 4 13:34:12 2022 kern.warn kernel: [2431717.616488] ieee80211_update_node_ecm_flags: node with aid 11 and mac c8:47:8c:01:23:45 has been tagged [ dvlan ]
Sun Dec 4 13:34:12 2022 kern.warn kernel: [2431717.616548] ath0: [c8:47:8c:01:23:45] station associated at aid 11: short preamble, long slot time, QoS, HT20 cap 0x431
Sun Dec 4 13:34:12 2022 user.info libubnt[3300]: wevent[3300]: wevent.ubnt_custom_event(): EVENT_STA_JOIN ath0: c8:47:8c:01:23:45 / 11
Sun Dec 4 13:34:12 2022 kern.warn kernel: [2431717.898425] ieee80211_update_node_ecm_flags: node with aid 11 and mac c8:47:8c:01:23:45 has been tagged [ dvlan rate limited ]
Sun Dec 4 13:34:13 2022 daemon.info hostapd[2220]: ath0: STA c8:47:8c:01:23:45 WPA: sending 1/4 msg of 4-Way Handshake
Sun Dec 4 13:34:14 2022 daemon.info hostapd[2220]: ath0: STA c8:47:8c:01:23:45 WPA: sending 1/4 msg of 4-Way Handshake
Sun Dec 4 13:34:15 2022 daemon.info hostapd[2220]: ath0: STA c8:47:8c:01:23:45 WPA: sending 1/4 msg of 4-Way Handshake
Sun Dec 4 13:34:16 2022 user.info libubnt[3300]: wevent[3300]: wevent.ubnt_custom_event(): EVENT_STA_LEAVE ath0: c8:47:8c:01:23:45 / 11
Sun Dec 4 13:34:21 2022 daemon.info hostapd[2220]: ath0: STA c8:47:8c:01:23:45 IEEE 802.11: deauthenticated due to local deauth request
Sun Dec 4 13:34:27 2022 daemon.info stahtd: stahtd[2217]: [STA-TRACKER].stahtd_dump_event(): {"message_type":"STA_ASSOC_TRACKER","auth_delta":"0","mac":"c8:47:8c:01:23:45","wpa_auth_failures":"1","vap":"ath0","auth_ts":"2431717.643499","assoc_delta":"10000","event_type":"failure","assoc_status":"0","event_id":"1"}
Sun Dec 4 13:34:35 2022 daemon.info stahtd: stahtd[2217]: [STA-TRACKER].stahtd_dump_event(): {"avg_rssi":"-84","dns_resp_seen":"yes","message_type":"STA_ASSOC_TRACKER","mac":"38:8b:59:48:d4:58","vap":"ath3","event_type":"fixup","assoc_status":"0","event_id":"10","arp_reply_gw_seen":"yes"}
Sun Dec 4 13:34:58 2022 daemon.info stahtd: stahtd[2217]: [STA-TRACKER].stahtd_dump_event(): {"avg_rssi":"-67","dns_resp_seen":"yes","message_type":"STA_ASSOC_TRACKER","mac":"f0:ef:86:24:68:1d","vap":"ath3","event_type":"fixup","assoc_status":"0","event_id":"4","arp_reply_gw_seen":"yes"}
Sun Dec 4 13:35:08 2022 daemon.info stahtd: stahtd[2217]: [STA-TRACKER].stahtd_dump_event(): {"avg_rssi":"-61","dns_resp_seen":"yes","message_type":"STA_ASSOC_TRACKER","mac":"9c:2e:a1:f4:d6:c9","vap":"ath3","event_type":"fixup","assoc_status":"0","event_id":"1","arp_reply_gw_seen":"yes"}
Sun Dec 4 14:29:54 2022 kern.warn kernel: [2435059.873629] ath0: [c8:47:8c:01:23:45] recv auth frame with algorithm 0 seq 1
Sun Dec 4 14:29:54 2022 daemon.info hostapd[2220]: ath0: STA fc:ec:da:8d:29:70 DRIVER: Send AUTH addr=c8:47:8c:01:23:45 status_code=0
Sun Dec 4 14:30:09 2022 daemon.info stahtd: stahtd[2217]: [STA-TRACKER].stahtd_dump_event(): {"message_type":"STA_ASSOC_TRACKER","mac":"c8:47:8c:01:23:45","vap":"ath0","auth_ts":"2435059.906830","auth_failures":"1","event_type":"failure","assoc_status":"0","event_id":"1"}
Sun Dec 4 14:30:19 2022 daemon.info hostapd[2220]: ath0: STA c8:47:8c:01:23:45 IEEE 802.11: disassociated
Sun Dec 4 14:42:43 2022 daemon.info hostapd[2220]: ath0: STA fc:ec:da:8d:29:70 DRIVER: Send AUTH addr=c8:47:8c:01:23:45 status_code=0
Sun Dec 4 14:42:43 2022 kern.warn kernel: [2435829.277311] ath0: [c8:47:8c:01:23:45] recv auth frame with algorithm 0 seq 1
Sun Dec 4 14:42:58 2022 daemon.info stahtd: stahtd[2217]: [STA-TRACKER].stahtd_dump_event(): {"message_type":"STA_ASSOC_TRACKER","mac":"c8:47:8c:01:23:45","vap":"ath0","auth_ts":"2435829.310535","auth_failures":"1","event_type":"failure","assoc_status":"0","event_id":"1"}
Sun Dec 4 14:43:06 2022 daemon.info hostapd[2220]: ath0: STA c8:47:8c:01:23:45 IEEE 802.11: disassociated
startDriver TuyaMCU
startDriver tmSensor
setChannelType 1 readonly
// link dpid to channel 1
linkTuyaMCUOutputToChannel 1 val 1

Quote:dpID может быть 1, 2 или 3, idk. Вам нужно проверить журналы.
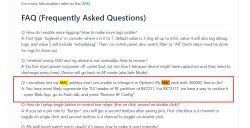
Quote:чип UNICMICRO UM8005
http://www.gztrchip.com/uploadfile/file/20210811/1628649277678726.pdf
его можно прошить?